Depending on how you look at it, Apple may be ramping up ways developers can reach out durectly to customers via its App Store – or building its own business at others’ expense.
What Apple is doing
Apple has had an advertising business of its own ever since Apple’s then CEO, Steve Jobs, introduced us to iAds in 2010. The scale of that offer was always limited to Apple’s platform, but the service arguably failed, with its technology living on in the form of ad slots in Apple News and the App Store.
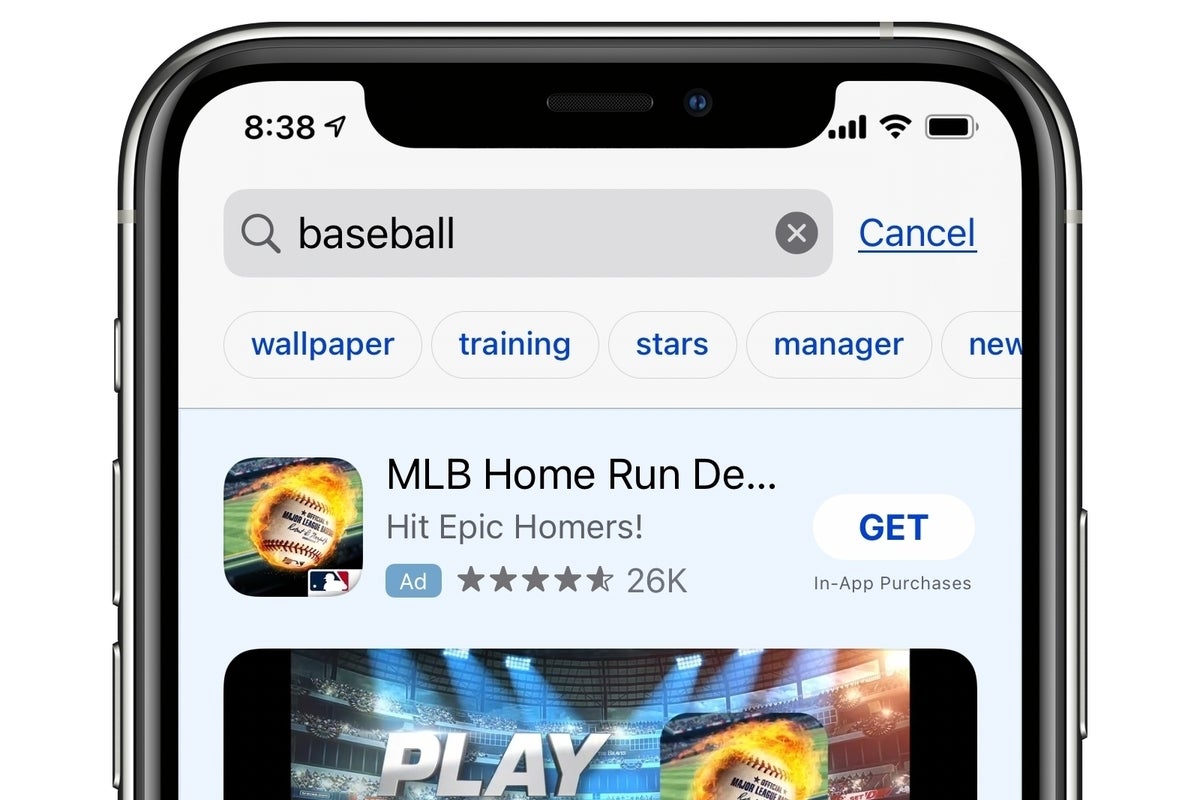
Apple’s App Store currently hosts just two ad slots, one in the search tab and the other in Search results. You can tell when you are looking at an ad from the blue shade behind the graphic and a small blue badge that says “ad” – these ads are hard to mistake for content.
To read this article in full, please click here