Phishing for Apples, Bobbing for Links
Credit to Author: BrianKrebs| Date: Mon, 13 Jan 2020 16:09:58 +0000
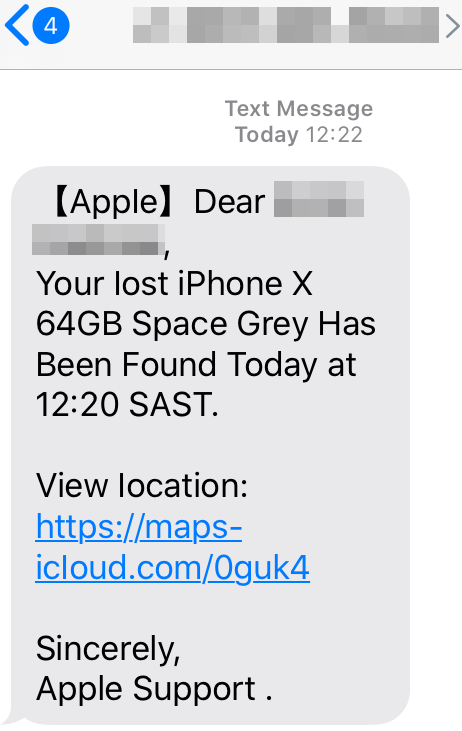
Anyone searching for a primer on how to spot clever phishing links need look no further than those targeting customers of Apple, whose brand by many measures has emerged as the most targeted. Past stories here have examined how scammers working with organized gangs try to phish iCloud credentials from Apple customers who have a mobile device that is lost or stolen. Today’s piece looks at the well-crafted links used in some of these lures.
Read more