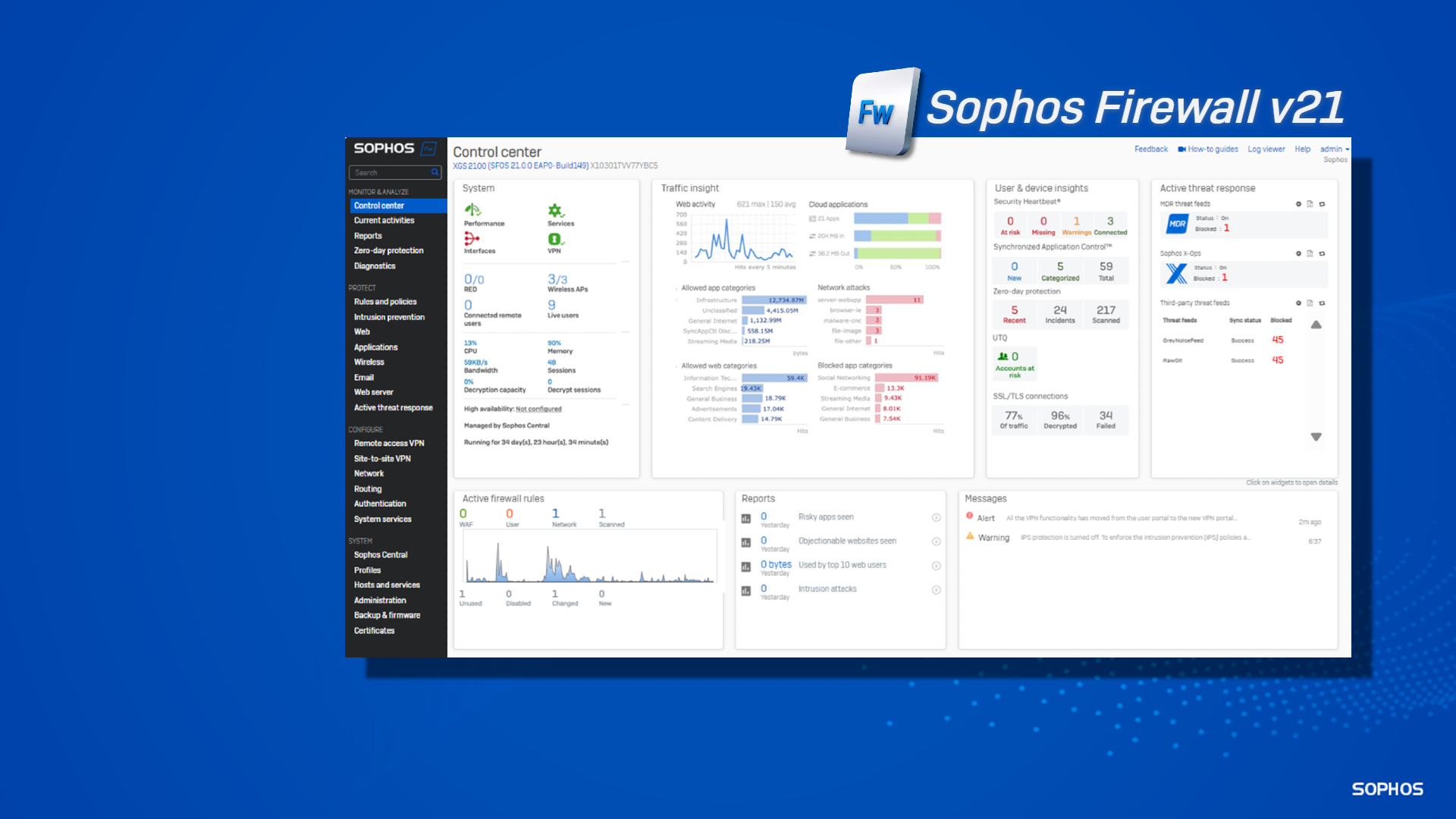
Upgrade your Sophos Firewall to v21 today
Credit to Author: Chris McCormack| Date: Wed, 04 Dec 2024 14:22:56 +0000
Get the most from your Sophos Firewall.
Read more
Credit to Author: Chris McCormack| Date: Wed, 04 Dec 2024 14:22:56 +0000
Get the most from your Sophos Firewall.
Read moreThe value of cryptocurrencies is going through the roof, so the scammers are even more interested in your funds
Read moreCredit to Author: Morton Swimmer| Date: Wed, 04 Dec 2024 00:00:00 +0000
Our research into Retrieval Augmented Generation (RAG) systems uncovered at least 80 unprotected servers. We highlight this problem, which can lead to potential data loss and unauthorized access.
Read more
Credit to Author: BrianKrebs| Date: Wed, 04 Dec 2024 14:08:45 +0000
In January 2022, KrebsOnSecurity identified a Russian man named Mikhail Matveev as “Wazawaka,” a cybercriminal who was deeply involved in the formation and operation of multiple ransomware groups. The U.S. government indicted Matveev as a top ransomware purveyor a year later, offering $10 million for information leading to his arrest. Last week, the Russian government reportedly arrested Matveev and charged him with creating malware used to extort companies.
Read more
Credit to Author: Lily Hay Newman| Date: Wed, 04 Dec 2024 14:00:00 +0000
The mobile device security firm iVerify has been offering a tool since May that makes spyware scanning accessible to anyone—and it’s already turning up victims.
Read more
Credit to Author: Lily Hay Newman| Date: Tue, 03 Dec 2024 20:19:37 +0000
At WIRED’s The Big Interview event, the president of the Signal Foundation talked about secure communications as critical infrastructure and the need for a new funding paradigm for tech.
Read more
Credit to Author: Dell Cameron, Dhruv Mehrotra| Date: Tue, 03 Dec 2024 19:18:29 +0000
The FTC is targeting data brokers that monitored people’s movements during protests and around US military installations. But signs suggest the Trump administration will be far more lenient.
Read more
Credit to Author: Andy Greenberg| Date: Tue, 03 Dec 2024 19:00:00 +0000
When programmer Micah Lee was kicked off X for a post that offended Elon Musk, he didn’t look back. His new tool for saving and deleting your X posts can give you that same sweet release.
Read moreAI chatbot provider WotNot left a cloud storage bucket exposed that contained almost 350,000 files, including personally identifiable information.
Read more
Credit to Author: rajansanhotra| Date: Tue, 03 Dec 2024 15:53:39 +0000
Sophos is the only vendor named a Customers’ Choice across Endpoint Protection Platforms, Network Firewalls, and Managed Detection and Response
Read more