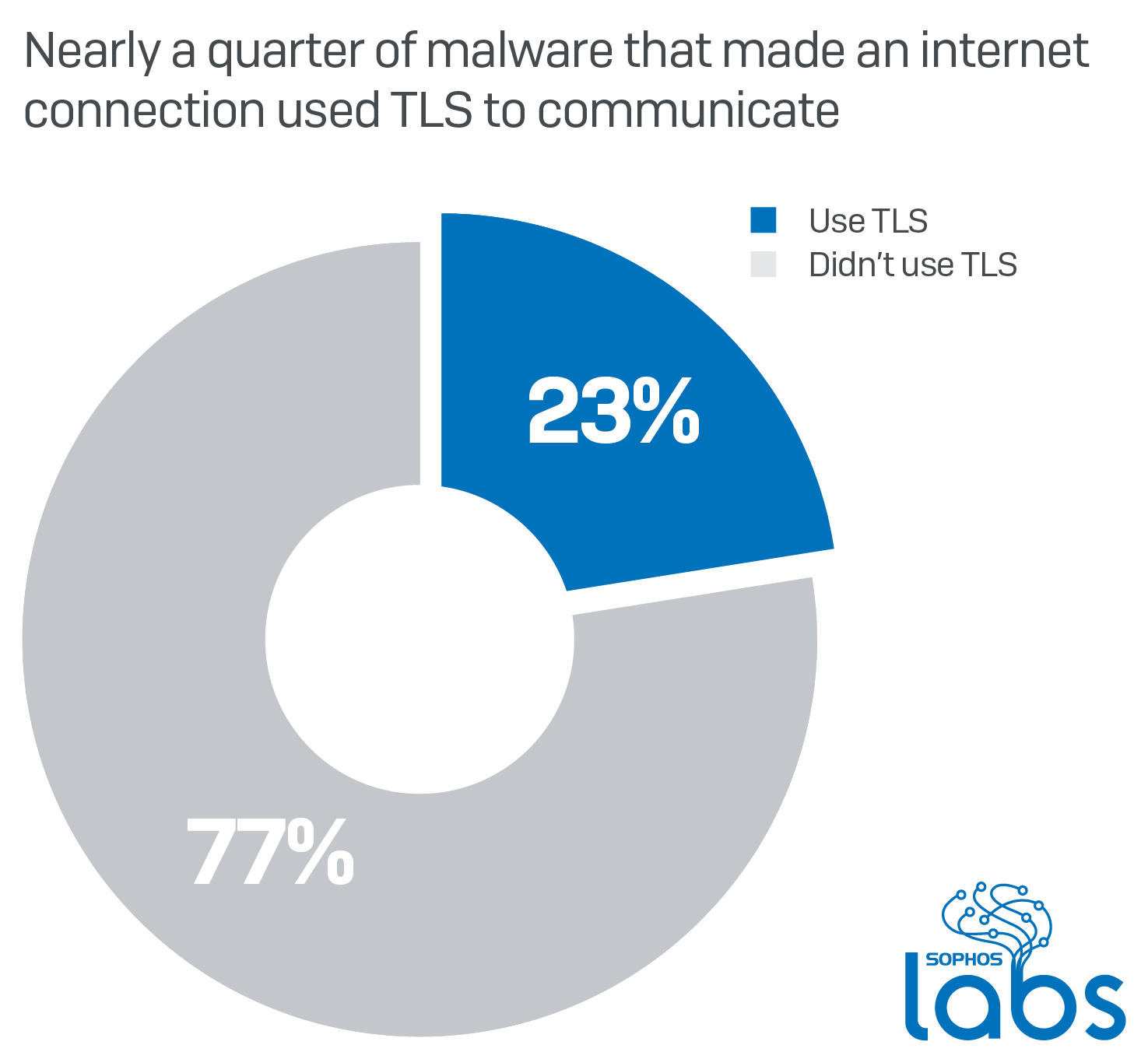
Nearly a quarter of malware now communicates using TLS
Credit to Author: Luca Nagy| Date: Tue, 18 Feb 2020 13:30:07 +0000
Encryption is one of the strongest weapons malware authors can leverage: They can use it to obfuscate their code, to prevent users (in the case of ransomware) from being able to access their files, and for securing their malicious network communication. As websites and apps more widely adopt TLS (Transport Layer Security) and communicate over […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/XXvUtjG7XVU” height=”1″ width=”1″ alt=””/>
Read more






