ChatGPT accused of breaking data protection rules
An Italian investigation into privacy concerns has given ChatGPT 30 days to defend itself.
Read moreAn Italian investigation into privacy concerns has given ChatGPT 30 days to defend itself.
Read more
Credit to Author: Kate O’Flaherty| Date: Wed, 31 Jan 2024 12:00:00 +0000
Plus: Google fixes dozens of Android bugs, Microsoft rolls out nearly 50 patches, Mozilla squashes 15 Firefox flaws, and more.
Read moreCredit to Author: Feike Hacquebord| Date: Wed, 31 Jan 2024 00:00:00 +0000
Based on our estimates, from approximately April 2022 until November 2023, Pawn Storm attempted to launch NTLMv2 hash relay attacks through different methods, with huge peaks in the number of targets and variations in the government departments that it targeted.
Read moreCredit to Author: Microsoft Threat Intelligence| Date: Mon, 29 Jan 2024 18:00:00 +0000
Jupyter notebooks are continuing to grow in popularity in information security as an alternative or supplement to mainstream security operations center (SOC) tools. Notebooks can be used interactively for threat detection and response, or as automated tasks in a larger pipeline. Their flexibility and ability to combine code, data analysis, and visualization in a single, […]
The post Join us at InfoSec Jupyterthon 2024 appeared first on Microsoft Security Blog.
Read moreCredit to Author: Jason Roszak| Date: Mon, 29 Jan 2024 17:00:00 +0000
This blog is the second of three that details our recommendation to adopt cloud native device management. Understand the lessons from various Intune customers in their journeys and how they achieved greater security, cost savings, and readiness for the future through their cloud transformations.
The post Best practices in moving to cloud native endpoint management appeared first on Microsoft Security Blog.
Read more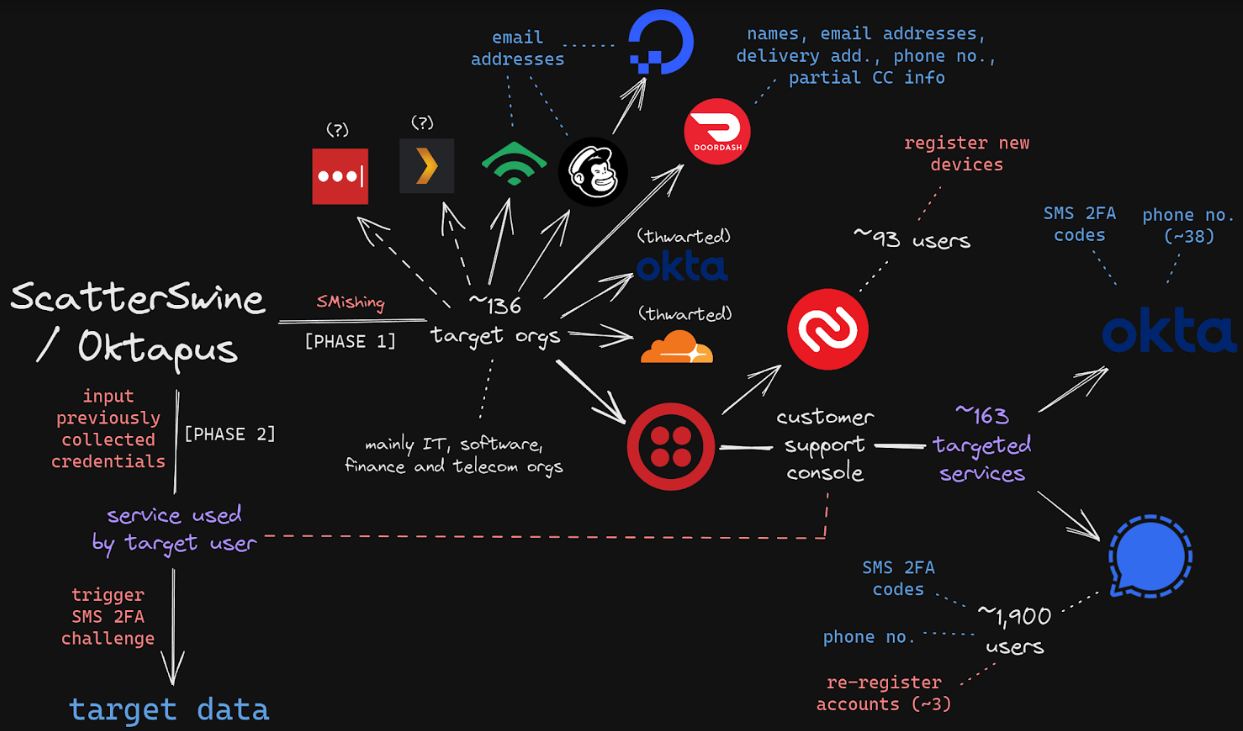
Credit to Author: BrianKrebs| Date: Tue, 30 Jan 2024 19:07:18 +0000
On Jan. 9, 2024, U.S. authorities arrested a 19-year-old Florida man charged with wire fraud, aggravated identity theft, and conspiring with others to use SIM-swapping to steal cryptocurrency. Sources close to the investigation tell KrebsOnSecurity the accused was a key member of a criminal hacking group blamed for a string of cyber intrusions at major U.S. technology companies during the summer of 2022.
Read more
In the name of security, the UK government may well have put a cybersecurity target on the nation’s back, with Apple once again warning that proposed changes to the Investigatory Powers Act 2016 are a “serious and direct threat to data security and information privacy.
“We are deeply concerned about the amendments to the Investigatory Powers Bill currently before Parliament, which will put the privacy and security of users at risk,” Apple said in a statement. “This is an unprecedented overreach by the government and, if implemented, the UK new user protections could be secretly vetoed globally, preventing us from ever delivering them to customers.”

Credit to Author: Matt Burgess| Date: Tue, 30 Jan 2024 12:00:00 +0000
Aerial drones have changed the war in Ukraine. Now, both Russia’s and Ukraine’s militaries are deploying more unmanned ground robots—and the two are colliding.
Read more
Credit to Author: Dell Cameron| Date: Mon, 29 Jan 2024 16:19:32 +0000
Members of Congress say the DOJ is funding the use of AI tools that further discriminatory policing practices. They’re demanding higher standards for federal grants.
Read moreTo comply with the EU’s Digital Markets Act, Apple will allow European iPhone owners to install apps obtained from outside the official App store.
Read more