Fujitsu Bugs That Sent Innocent People to Prison Were Known ‘From the Start’

Credit to Author: Jon Brodkin, Ars Technica| Date: Sat, 20 Jan 2024 18:00:00 +0000
Software flaws were allegedly hidden from lawyers of wrongly convicted UK postal workers.
Read moreUS Agencies Urged to Patch Ivanti VPNs That Are Actively Being Hacked

Credit to Author: Lily Hay Newman| Date: Sat, 20 Jan 2024 14:00:00 +0000
Plus: Microsoft says attackers accessed employee emails, Walmart fails to stop gift card fraud, “pig butchering” scams fuel violence in Myanmar, and more.
Read moreMicrosoft at Legalweek: Secure data and gain efficiencies with Microsoft Purview eDiscovery enhanced by generative AI
Credit to Author: Caitlin Fitzgerald| Date: Thu, 18 Jan 2024 17:00:00 +0000
Microsoft solutions can ease some of the top challenges of legal professionals. Read on for two advantages of the combination of Microsoft Purview eDiscovery and generative AI, and explore opportunities to connect with us at Legalweek.
The post Microsoft at Legalweek: Secure data and gain efficiencies with Microsoft Purview eDiscovery enhanced by generative AI appeared first on Microsoft Security Blog.
Read moreNew Microsoft Incident Response guides help security teams analyze suspicious activity
Credit to Author: Microsoft Incident Response| Date: Wed, 17 Jan 2024 18:00:00 +0000
Access the first two cloud investigation guides from Microsoft Incident Response to improve triage and analysis of data in Microsoft 365 and Microsoft Entra ID.
The post New Microsoft Incident Response guides help security teams analyze suspicious activity appeared first on Microsoft Security Blog.
Read moreNew TTPs observed in Mint Sandstorm campaign targeting high-profile individuals at universities and research orgs
Credit to Author: Microsoft Threat Intelligence| Date: Wed, 17 Jan 2024 17:00:00 +0000
Since November 2023, Microsoft has observed a distinct subset of Mint Sandstorm (PHOSPHORUS) targeting high-profile individuals working on Middle Eastern affairs at universities and research organizations in Belgium, France, Gaza, Israel, the United Kingdom, and the United States. In this campaign, the threat actor used bespoke phishing lures in an attempt to socially engineer targets into downloading malicious files.
The post New TTPs observed in Mint Sandstorm campaign targeting high-profile individuals at universities and research orgs appeared first on Microsoft Security Blog.
Read moreGoogle failing to scrub abortion access in location history, study claims
A nonprofit study claims that Google is failing to delete location history that reveals users’ physical trips to abortion clinics.
Read moreProtecting Your Network Security from Ivanti Zero-Day Threat
Credit to Author: Chris LaFleur| Date: Thu, 18 Jan 2024 00:00:00 +0000
The overlooked vulnerability with real impacts
Read moreCanadian Man Stuck in Triangle of E-Commerce Fraud
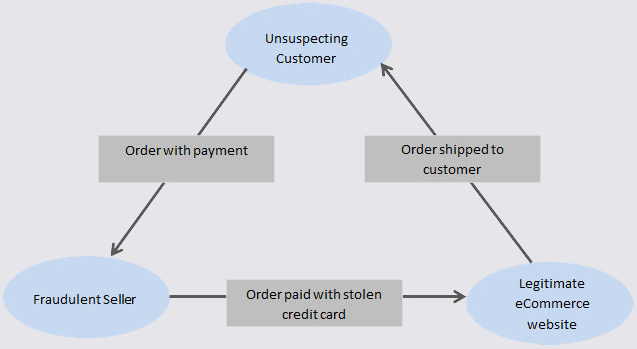
Credit to Author: BrianKrebs| Date: Fri, 19 Jan 2024 15:34:53 +0000
A Canadian man who says he’s been falsely charged with orchestrating a complex e-commerce scam is seeking to clear his name. His case appears to involve “triangulation fraud,” which occurs when a consumer purchases something online — from a seller on Amazon or eBay, for example — but the seller doesn’t actually own the item for sale. Instead, the seller purchases the item from an online retailer using stolen payment card data. In this scam, the unwitting buyer pays the scammer and receives what they ordered, and very often the only party left to dispute the transaction is the owner of the stolen payment card.
Read more