Apple to introduce new feature that makes life harder for iPhone thieves
Apple has plans to make it harder for iPhone thieves to steal your personal information even if they have your device’s passcode.
Read moreApple has plans to make it harder for iPhone thieves to steal your personal information even if they have your device’s passcode.
Read moreA recently patched Apache Struts 2 vulnerability has been spotted in worldwide exploitation attempts. Users and admins should update ASAP.
Read moreCredit to Author: Alifiya Sadikali| Date: Thu, 14 Dec 2023 00:00:00 +0000
Today’s attack surface requires modern processes and security solutions. Explore the tenants of modern attack surface management (ASM) and what SecOps need to look for in an ASM solution.
Read moreApple has changed its legal process guidelines so it now requires a judge’s order to hand over information about its customers’ push notifications.
Read more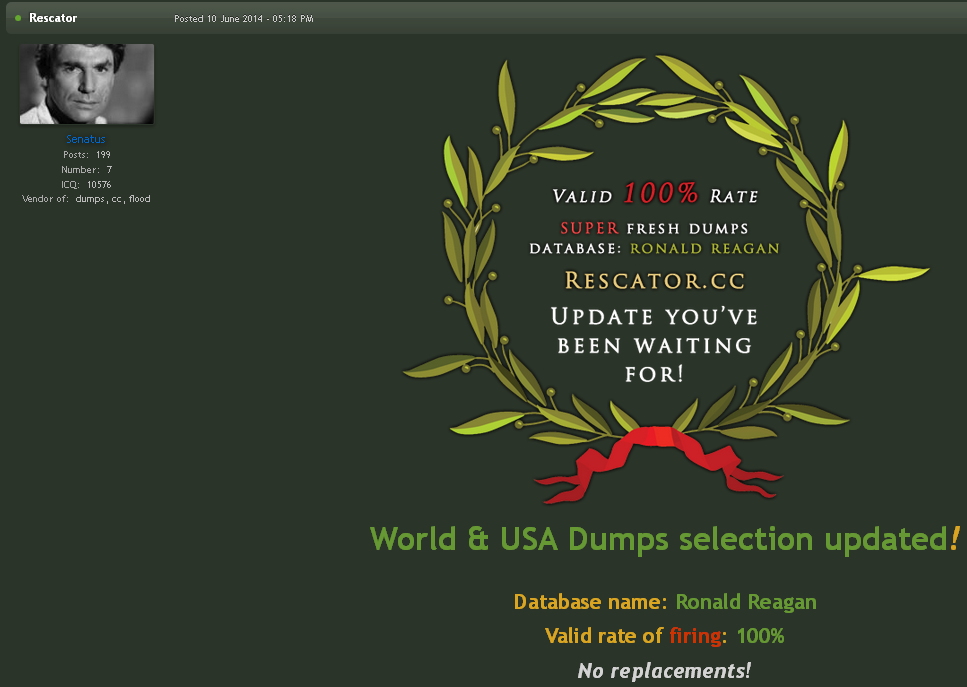
Credit to Author: BrianKrebs| Date: Thu, 14 Dec 2023 17:51:39 +0000
On Dec. 18, 2013, KrebsOnSecurity broke the news that U.S. retail giant Target was battling a wide-ranging computer intrusion that compromised more than 40 million customer payment cards over the previous month. The malware used in the Target breach included the text string “Rescator,” which also was the handle chosen by the cybercriminal who was selling all of the cards stolen from Target customers. Ten years later, KrebsOnSecurity has uncovered new clues about the real-life identity of Rescator.
Read more
Credit to Author: Chester Wisniewski| Date: Thu, 14 Dec 2023 18:08:41 +0000
Why the new US regulatory disclosure requirements work for the defenders, not the criminals
Read moreApple has changed its legal process guidelines to reflect it now requires a judge’s order to hand over information about its customers’ push notifications.
Read more
Credit to Author: Andy Greenberg| Date: Wed, 13 Dec 2023 15:56:43 +0000
A hacker group calling itself Solntsepek—previously linked to Russia’s notorious Sandworm hackers—says it carried out a disruptive breach of Kyivstar, a major Ukrainian mobile and internet provider.
Read moreCredit to Author: Microsoft Threat Intelligence| Date: Tue, 12 Dec 2023 18:00:00 +0000
Microsoft Threat Intelligence presents cases of threat actors misusing OAuth applications as automation tools in financially motivated attacks.
The post Threat actors misuse OAuth applications to automate financially driven attacks appeared first on Microsoft Security Blog.
Read more