Scammers Are Scamming Other Scammers Out of Millions of Dollars

Credit to Author: Matt Burgess| Date: Wed, 07 Dec 2022 17:01:33 +0000
On cybercrime forums, user complaints about being duped may accidentally expose their real identities.
Read more
Credit to Author: Matt Burgess| Date: Wed, 07 Dec 2022 17:01:33 +0000
On cybercrime forums, user complaints about being duped may accidentally expose their real identities.
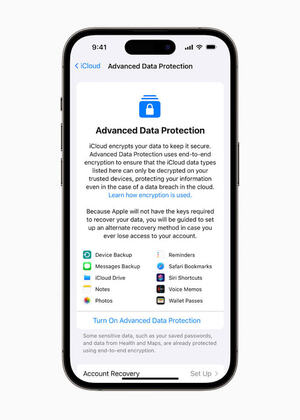
Read moreApple today introduced several new security features focused on fending off threats to user data in the cloud, including end-to-end encryption for backups for iCloud users.
Along with end-to-end encryption for iCloud, Apple’s cloud storage and computing platform, the company announced iMessage Contact Key Verification, allowing users to verify they are communicating only with whom they intend.
 Apple
AppleApple also announced hardware Security Keys for Apple ID, giving users the choice to require two-factor authentication to sign into their Apple ID account. (Hardware security keys use devices, such as USB thumb drives or near-field communication (NFC) dongles, to enable access to a service or application.)
Credit to Author: Microsoft Security Threat Intelligence| Date: Wed, 07 Dec 2022 17:00:00 +0000
The updated threat matrix for Kubernetes comes in a new format that simplifies usage of the knowledge base and with new content to help mitigate threats.
The post Mitigate threats with the new threat matrix for Kubernetes appeared first on Microsoft Security Blog.
Read more
Credit to Author: Sanjana Varghese| Date: Tue, 06 Dec 2022 13:22:46 +0000
The UK’s use of technology to enforce its hard-line immigration policy brings the border into every facet of migrants’ lives.
Read more
Three years and four prime ministers after the UK government first published its Online Harms white paper—the basis for the current Online Safety Bill—the Conservative Party’s ambitious attempt at internet regulation has found its way back to Parliament after multiple amendments.
If the bill becomes law, it will apply to any service or site that has users in the UK, or targets the UK as a market, even if it is not based in the country. Failure to comply with the proposed rules will place organizations at risk of fines of up to 10% of global annual turnover or £18 million (US$22 million), whichever is higher.
A somewhat bloated and confused version of its former self, the bill, which was dropped from the legislative agenda when Boris Johnson was ousted in July, has now passed its final report stage, meaning the House of Commons now has one last chance to debate its contents and vote on whether to approve it.
Credit to Author: Katie McCafferty| Date: Tue, 06 Dec 2022 17:00:00 +0000
Microsoft security researchers investigate an attack where the threat actor, tracked DEV-0139, used chat groups to target specific cryptocurrency investment companies and run a backdoor within their network.
The post DEV-0139 launches targeted attacks against the cryptocurrency industry appeared first on Microsoft Security Blog.
Read more
Credit to Author: Sanjana Varghese| Date: Tue, 06 Dec 2022 13:22:46 +0000
The UK’s use of technology to enforce its hard-line immigration policy brings the border into every facet of migrants’ lives.
Read more
Credit to Author: eschuman@thecontentfirm.com| Date: Mon, 05 Dec 2022 09:43:00 -0800
Biometrics is supposed to be one of the underpinnings of a modern authentication system. But many biometric implementations (whether that be fingerprint scanes or face recognition) can be wildly inaccurate, and the only universally positive thing to say about them is they’re better than nothing.
Also — and this may prove critical — the fact that biometrics are falsely seen as being very accurate may be sufficient to dissuade some fraud attempts.
There are a variety of practical reasons biometrics don’t work well in the real world, and a recent post by a cybersecurity specialist at KnowBe4, a security awareness training vendor, adds a new layer of complexity to the biometrics issue.

Credit to Author: Dhruv Mehrotra| Date: Sat, 03 Dec 2022 14:00:00 +0000
Plus: ICE accidentally doxes asylum seekers, Google fails to uphold a post-Roe promise, and LastPass suffers the second breach this year.
Read more.jpg)
Credit to Author: Lily Hay Newman| Date: Fri, 02 Dec 2022 19:19:31 +0000
Device manufacturers use “platform certificates” to verify an app’s authenticity, making them particularly dangerous in the wrong hands.
Read more