Hackers Hit Click2Gov Bill-Paying Portals in 8 Cities

Credit to Author: Dan Goodin, Ars Technica| Date: Sat, 21 Sep 2019 12:00:00 +0000
The new wave of attacks comes after a previous Click2Gov hack compromised 300,000 payment cards.
Read more
Credit to Author: Dan Goodin, Ars Technica| Date: Sat, 21 Sep 2019 12:00:00 +0000
The new wave of attacks comes after a previous Click2Gov hack compromised 300,000 payment cards.
Read more
Credit to Author: Klint Finley| Date: Fri, 20 Sep 2019 00:06:13 +0000
An international cybersecurity group has evicted the Chinese telecom company to comply with US sanctions. That could allow malware to spread more easily.
Read more
Credit to Author: Jonny Evans| Date: Mon, 23 Sep 2019 07:56:00 -0700
Apple may place much of its focus on Apple Arcade and consumer-friendly iPad/iPhone features, but there are numerous enterprise-focused enhancements wrapped up inside iOS 13.
The company’s latest operating systems introduce a host of productivity-enhancing upgrades, particularly for the iPad.
Yet the biggest improvements specifically for enterprise users aim to make a more robust division between personal and enterprise data for Bring Your Own Device (BYOD) deployments, solving one of the big challenges in the space.
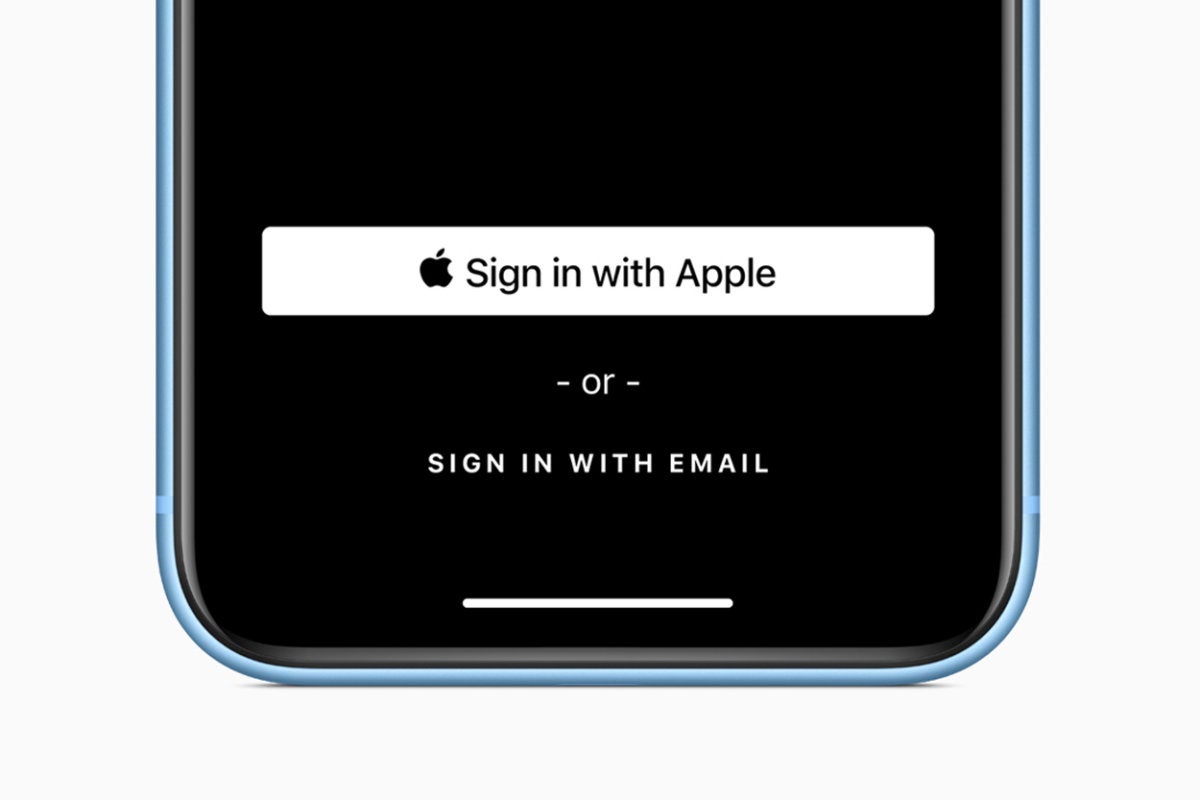
Credit to Author: Jonny Evans| Date: Fri, 20 Sep 2019 05:29:00 -0700
If you’ve (successfully) upgraded to iOS 13 or just got hold of a new iPhone 11 or 11 Pro, there are new security settings in Apple’s latest operating system you need to learn and use. Here’s what’s important to understand.
There were 26.3 billion robocalls in the U.S. in 2018. It’s a a sickness.
You can stop the contagion thanks to a new in iOS 13 feature that directs incoming calls from unknown numbers (ie. those you don’t have in your Contacts book) to voicemail. It’s a useful feature that isn’t enabled by default.
Credit to Author: Ed Cabrera (Chief Cybersecurity Officer)| Date: Fri, 20 Sep 2019 14:40:18 +0000

We have been collectively saying in our industry for the last 15-20 years that a layered approach to your security stack is a “best practice,” but as with all best practices, these are ideals rather than reality for so many charged with protecting their organizations. The vast majority of CISOs are saddled with legacy operating…
The post Why Should CISOs Care About XDR? appeared first on .
Read moreCredit to Author: Jon Clay (Global Threat Communications)| Date: Fri, 20 Sep 2019 13:05:20 +0000

Welcome to our weekly roundup, where we share what you need to know about the cybersecurity news and events that happened over the past few days. This week, learn about Magecart attacks and the security implications of PSD2. Also, read about how your smart TV might be leaking your data to the likes of Facebook,…
The post This Week in Security News: Magecart Attacks and Is Your Smart TV Spying on You? appeared first on .
Read moreCredit to Author: Ed Cabrera (Chief Cybersecurity Officer)| Date: Thu, 19 Sep 2019 13:53:11 +0000

Verizon recently released a 5 step process for evaluating cloud security products and services to inform purchase decisions. That’s a fantastic tool for buyers to have. This is especially helpful because cloud discussions are almost always driven by business objectives to satisfy a cost and or productivity problem. The CISO has to come in and…
The post Beyond The Standard CISO Cloud Security Guide appeared first on .
Read more
Credit to Author: Lily Hay Newman| Date: Wed, 18 Sep 2019 21:41:59 +0000
New research shows that over 2,000 streaming apps track information about your devices—even when you tell them not to.
Read more
Credit to Author: Sharky| Date: Thu, 19 Sep 2019 03:00:00 -0700
It’s 1977, and this pilot fish’s company is moving to a new data center. “The old facility was in the basement of the headquarters building,” says fish. “Access was via an ancient magnetic strip reader with no special capabilities. You either got in or you didn’t.
The new facility has state-of-the-art card readers, supported by a small midrange system. It has lots of capabilities — which can be a bit of trouble when you have a security department that’s paranoid about access to the facility.
And trouble does arrive, about a month after the move to the new building, when the security department programs the system to allow admission only during scheduled working hours.

Credit to Author: Lily Hay Newman| Date: Wed, 18 Sep 2019 13:00:00 +0000
By exploiting the WS-Discovery protocol, a new breed of DDoS attack can get a huge rate of return.
Read more