How the most damaging ransomware evades IT security
Credit to Author: Mark Loman| Date: Thu, 14 Nov 2019 13:50:28 +0000
Ransomware has been around for decades, yet it remains a common and lucrative cyberthreat. We decided to take a closer look at the behaviour of ransomware once it is inside a victim system, and how the various tools and techniques observed are used by the most prevalent ransomware families, from WannaCry, Matrix and GandCrab to Ryuk, SamSam, MegaCortex, and more. This article is a summary of a report we’re releasing today, How Ransomware Attacks: What defenders should know about the most prevalent and persistent ransomware families.
New ransomware variants are created and released every day and the job of security software is to detect and block them before they do any harm. The result is a continuous struggle between defenders, with their security controls and detection systems finely tuned to spot suspicious code and behavior, and adversaries, with their ever evolving bag of tricks designed to outfox these controls – or to get the job done before the controls catch up with them.
Every journey starts with a suitcasev
The first hurdle for security software is often the packer the malicious code is wrapped and delivered in. Proprietory packers or those with heavily obfuscated code make it hard for protection technologies to see what’s inside (the malicious executable) and what its intentions are, and to respond accordingly.
The next hurdle is to detect and mitigate the actions of the malware once it is unpacked inside the system. Since endpoint protection software is on the lookout for potentially malicious behavior, it will come as no surprise that adversaries are focused on making everything look legitimate until they have achieved their purpose: encrypted your data and made it very difficult if not impossible for you to get it back without paying the ransom demanded.
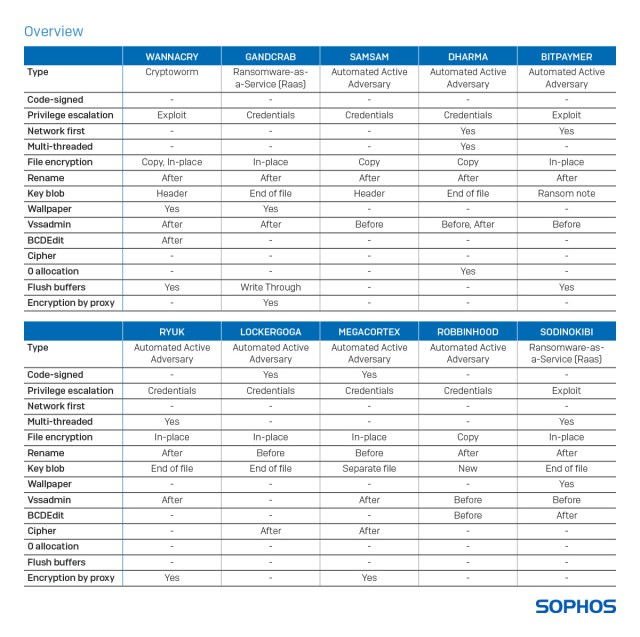
Nothing to declare
The list of techniques employed by ransomware to avoid arousing suspicion is long, and includes the following:
Code signing
Attackers may attempt to minimize detection by signing their ransomware with a legitimate authentication certificate, which may help the ransomware evade unsigned-code detection by some software security tools. There are a few risks with this approach, however. To acquire an Authenticode code-signing certificate, you need to buy (or steal) one, and share both payment and contact details. This means that discovery can lead not just to the certificate being revoked (and all malware signed with it to be quarantined), but possibly to the identification of the attackers behind the ransomware.
Privilege escalation
Restricting data access rights is a basic security practice, but sadly an increasingly ineffective one. There are a number of exploits that allow attackers to elevate privileges and abuse stolen administrator credentials, regardless of the access rights of the compromised user.
Examples include the infamous EternalBlue exploit used by WannaCry, as well as an exploit for the User Access Control (UAC) prompt, which allows any ransomware to be launched with elevated privileges. There is also one that enables attackers to run arbitrary code in kernel mode and, as a result, to install programs, view, change, or delete data, or create new accounts with full user rights – regardless of the privileges of the logged in user.
Lateral movement
Once a server or endpoint has been compromised, the attackers can disable the security software, install a remote access tool (RAT) for flexibility and persistence and go hunting for data file and backup servers. They can take control of a server via the Remote Desktop Protocol (RDP) and destroy the data backups via ransom encryption or simple deletion, to ensure the victim cannot recover. Lastly, they can distribute ransomware to peer endpoints and file servers.
To do this they may leverage a trusted dual-use utility, crafting a script that copies and executes the ransomware onto computers. This generally takes less than an hour to complete, and typically happens during the night when the IT team is at home asleep. By the time the victim spots what’s going on it is too late.
Attackers have also been observed leveraging stolen credentials for, or exploiting vulnerabilities in remote monitoring and management (RMM) solutions typically used by Managed Service Providers (MSP) to manage customers’ IT infrastructure and/or end-user systems.
Network first
To ensure victims pay up, ransomware will try to encrypt as many documents as possible, as quickly as possible and then make it hard, if not impossible for earlier or duplicate versions to be recovered.
Documents are often stored on local fixed and removable drives, as well as on mapped remote shared drives. The ransomware might prioritize certain drives or document sizes first, to ensure success before being caught by endpoint protection software or noticed by victims. For example, the ransomware may be programmed to encrypt several documents at the same time via multiple threads, prioritize smaller documents or even start by attacking documents on mapped remote shared drives.
It is important to mention that the file servers themselves are often not infected with the ransomware. The threat typically runs on one or more compromised endpoints, abusing a privileged user account with administrator-level permissions to remotely attack the documents. So even if the file server is protected by antivirus software, the threat itself is not actually running on the server.
Multi-threaded
Computers now have one or more multi-core central processing units (CPUs) with Simultaneous Multithreading (SMT) or Hyper-Threading (HT) technology. Such advances in microprocessor hardware offer huge performance benefits for day-to-day business operations, as they allow parallel execution and better system utilization to speed up productivity. Some ransomware, designed to make efficient use of modern CPU hardware, takes advantage of this feature (if present) to parallelize individual tasks. If speed is the name of the ransomware game, this helps ensure faster (and, greater) impact, before victims discover they’re under attack.
Among other things, data in a faster medium (such as memory) can be retrieved by one thread while another thread retrieves data from a slower medium (such as storage), with neither thread waiting for the other to finish.
File encryption and renaming
Based on how it encrypts documents, ransomware can be divided into two groups: Overwrite and Copy.
There are examples of ransomware creating encrypted copies of the documents they attack and then deleting the original files afterwards. In this case the encrypted copies are stored elsewhere on the storage drive. In order to prevent a data recovery product from retrieving the original files via an undelete, one ransomware family, Dharma sets the file size of each of the attacked documents to 0 bytes before deletion.
Encryption by proxy
Some ransomware – like GandCrab and Sodinokibi – abuse Windows PowerShell to pull in a PowerShell script from the internet, which is set to automatically start the ransomware after a delay of several days, making the attack appear to come out of nowhere. In this scenario, the actual file encryption attack itself is performed by the trusted Windows POWERSHELL.EXE process, tricking the security software into thinking a trusted application is modifying the documents. Other ransomware like Ryuk and MegaCortex use a similar approach to encrypt documents from a trusted process.
Don’t give up
Our review of the behavior of ransomware is intended to help IT security professionals and their service providers better understand the tools and techniques deployed by this threat as it moves through an affected system.
It is extremely important to complement insight and intelligence with appropriate security policies and protection technologies. This includes implementing practical measures such as enabling Multi-Factor Authentication (MFA) on central management tools and leaving Tamper Protection on endpoint protection software turned on; as well as keeping an eye on the correct configuration of all connected systems and applying security patches whenever they are released.
Last, but definitely not least, ensure you have advanced, multi-layered security software installed. Security products such as Sophos Intercept X protect local fixed and removable drives, as well as mapped remote shared drives and shared local folders – on both endpoint and servers.