Fake Emergency Search Warrants Draw Scrutiny from Capitol Hill
Credit to Author: BrianKrebs| Date: Thu, 31 Mar 2022 22:54:45 +0000
On Tuesday, KrebsOnSecurity warned that hackers increasingly are using compromised government and police department email accounts to obtain sensitive customer data from mobile providers, ISPs and social media companies. Today, one of the U.S. Senate’s most tech-savvy lawmakers said he was troubled by the report and is now asking technology companies and federal agencies for information about the frequency of such schemes.

At issue are forged “emergency data requests,” (EDRs) sent through hacked police or government agency email accounts. Tech companies usually require a search warrant or subpoena before providing customer or user data, but any police jurisdiction can use an EDR to request immediate access to data without a warrant, provided the law enforcement entity attests that the request is related to an urgent matter of life and death.
As Tuesday’s story showed, hackers have figured out there is no quick and easy way for a company that receives one of these EDRs to know whether it is legitimate. After all, there are roughly 18,000 distinct police organizations in the United States alone, and many thousands of government and police agencies worldwide.
Criminal hackers exploiting that ambiguity are enjoying remarkable success rates gaining access to the data they’re after, and some are now selling EDRs as a service to other crooks online.
This week’s piece included confirmation from social media platform Discord about a fraudulent EDR they recently processed. On Wednesday, Bloomberg published a story confirming that both Apple and Meta/Facebook have recently complied with fake EDRs.
Today, KrebsOnSecurity heard from Sen. Ron Wyden (D-Ore.), who said he was moved to action after reading this week’s coverage.
“Recent news reports have revealed an enormous threat to Americans’ safety and national security,” Wyden said in a statement provided to KrebsOnSecurity. “I’m particularly troubled by the prospect that forged emergency orders may be coming from compromised foreign law enforcement agencies, and then used to target vulnerable individuals.”
“I’m requesting information from tech companies and multiple federal agencies to learn more about how emergency data requests are being abused by hackers,” Wyden’s statement continues. “No one wants tech companies to refuse legitimate emergency requests when someone’s safety is at stake, but the current system has clear weaknesses that need to be addressed. Fraudulent government requests are a significant concern, which is why I’ve already authored legislation to stamp out forged warrants and subpoenas.”
Tuesday’s story showed how fraudulently obtained EDRs were a tool used by members of LAPSUS$, the data extortion group that recently hacked Microsoft, NVIDIA, Okta and Samsung. And it tracked the activities of a teenage hacker from the United Kingdom who was reportedly arrested multiple times for sending fake EDRs.
That was in March 2021, but there are similar fake EDR services on offer today. One example can be found on Telegram, wherein a member who favors the handle “Bug” has for the past month been selling access to various police and government email accounts.
All of the access Bug is currently offering was allegedly stolen from non-U.S. police and government email accounts, including a police department in India; a government ministry of the United Arab Emirates; the Brazilian Secretariat of Education; and Saudi Arabia’s Ministry of Education.
On Mar. 30, Bug posted a sales thread to the cybercrime forum Breached[.]co saying he could be hired to perform fake EDRs on targets at will, provided the account was recently active.
“I am doing LE Emergency Data Requests for snapchat, twitter, ig [Instagram] and many others,” Bug wrote. “Information we can get: emails, IPs, phone numbers, photos. Account must be active in the last week else we get rejected as shown below. Have gotten information only on Snapchat, Twitter and IG so far.”
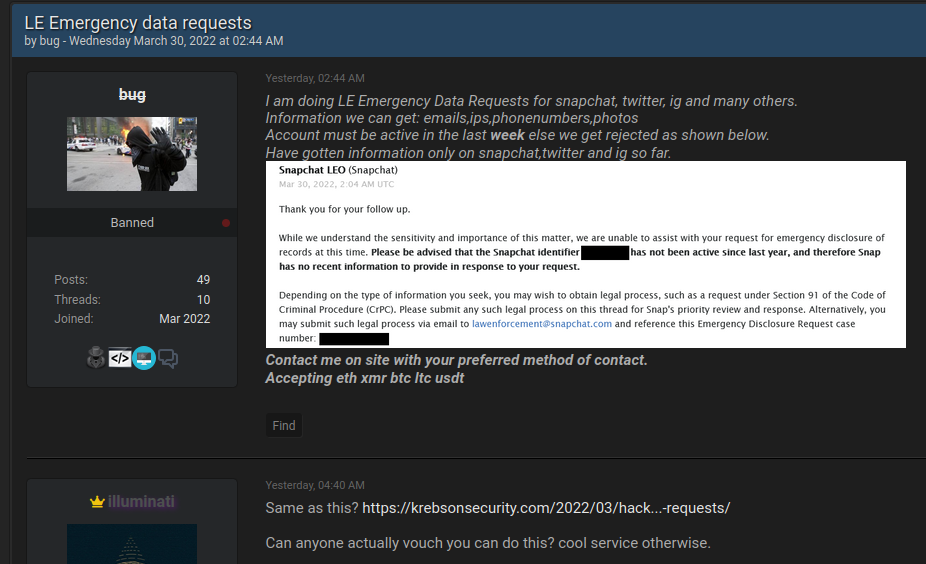
An individual using the nickname “Bug” has been selling access to government and police email accounts for more than a month. Bug posted this sales thread on Wednesday.
KrebsOnSecurity sought comment from Instagram, Snapchat, and Twitter. This post will be updated in the event they respond.
The current scourge of fraudulent EDRs illustrates the dangers of relying solely on email to process legal requests for privileged subscriber data. In July 2021, Sen. Wyden and others introduced new legislation to combat the growing use of counterfeit court orders by scammers and criminals. The bill calls for funding for state and tribal courts to adopt widely available digital signature technology that meets standards developed by the National Institute of Standards and Technology.
“Forged court orders, usually involving copy-and-pasted signatures of judges, have been used to authorize illegal wiretaps and fraudulently take down legitimate reviews and websites by those seeking to conceal negative information and past crimes,” the lawmakers said in a statement introducing their bill.
The Digital Authenticity for Court Orders Act would require federal, state and tribal courts to use a digital signature for orders authorizing surveillance, domain seizures and removal of online content.