Active Adversary Playbook 2022 Insights: Web Shells
Credit to Author: gallagherseanm| Date: Wed, 22 Jun 2022 11:00:07 +0000
Every year, certain events stand out in the data we review for the Active Adversary Playbook more than others, and 2021 was no exception. A few incidents emerged that provided additional insight that we felt deserved additional focus—particularly several that demonstrated the perils of public disclosure of proof-of-concept exploits that can be leveraged for web shells.
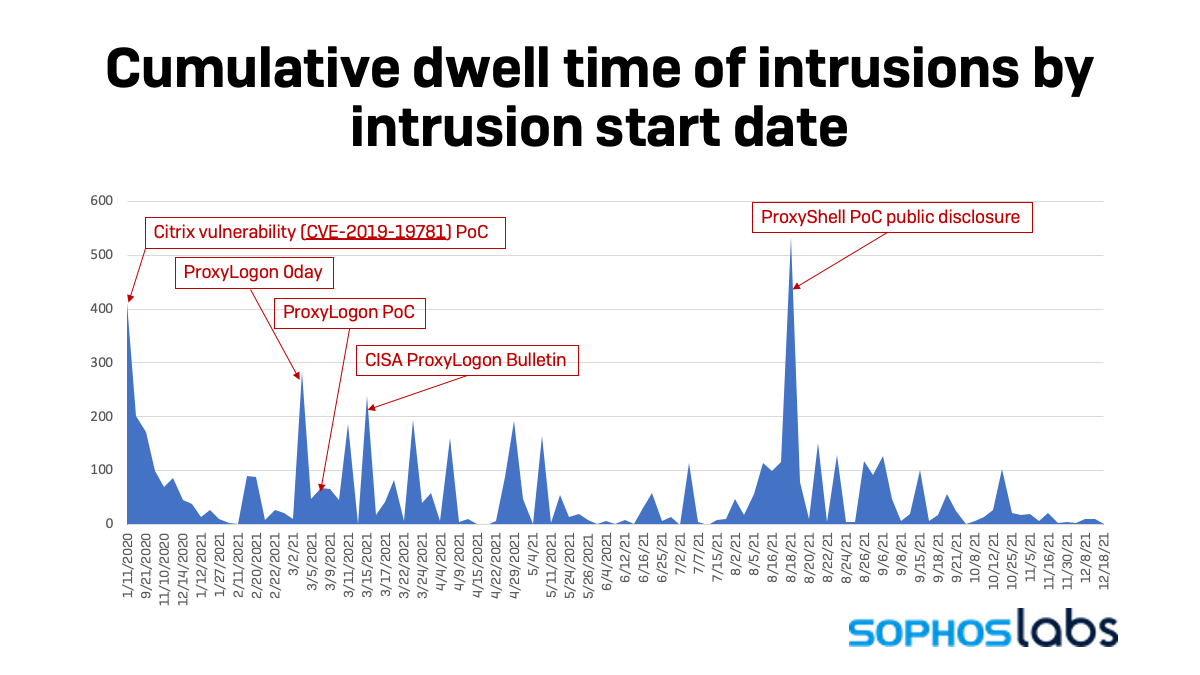
While querying the data for interesting correlations, a few spikes appeared in the dwell time statistics. These spikes corresponded closely to the publication date of POC exploits for known vulnerabilities.
The first spike in January 2021 was the result of an exploited Citrix vulnerability (CVE-2019-19781). This exploit led to an intrusion, but no clear motive for the activity was determined. This intrusion accounted for the largest dwell time figure in our main report. It also was the first example of a correlation that we would see repeat in the coming months. While the Citrix bulletin for the vulnerability was released on December 27 of 2019, the proof of concept (POC) exploit for the vulnerability was released on January 11, 2021—which coincided with the start of this attack.
The following spikes, on the 3rd and 15th of March respectively, can be attributed to the exploitation of the ProxyLogon 0-day vulnerability. Microsoft’s bulletin was released on March 02, although there was detected activity prior to the bulletin’s release. On the following day we saw a spike of victims. Then, on March 9, a public POC exploit was released, and on March 14 a CISA bulletin was released. A second spike followed on March 15. In total, there were 16 victims that resulted from unpatched ProxyLogon vulnerabilities.
The last spike demonstrates a much tighter correlation between disclosure and exploitation. As noted by the Sophos News coverage of this vulnerability, ProxyShell comprises three separate vulnerabilities used as part of a single attack chain:
- CVE-2021-34473: Pre-auth path confusion vulnerability to bypass access control
- CVE-2021-34523: Privilege elevation vulnerability in the Exchange PowerShell backend
- CVE-2021-31207: Post-auth remote code execution via arbitrary file write
This carefully crafted attack chain was demonstrated at Pwn2Own, presented at Black Hat, and the POC was publicly disclosed on August 18. On this day we saw 7 organizations immediately fall victim to this attack. There was a total of 40 victims that can be attributed to ProxyShell exploitation, and we have seen continued exploitation of both the ProxyLogon and ProxyShell vulnerabilities into 2022.
Web Shells going the distance
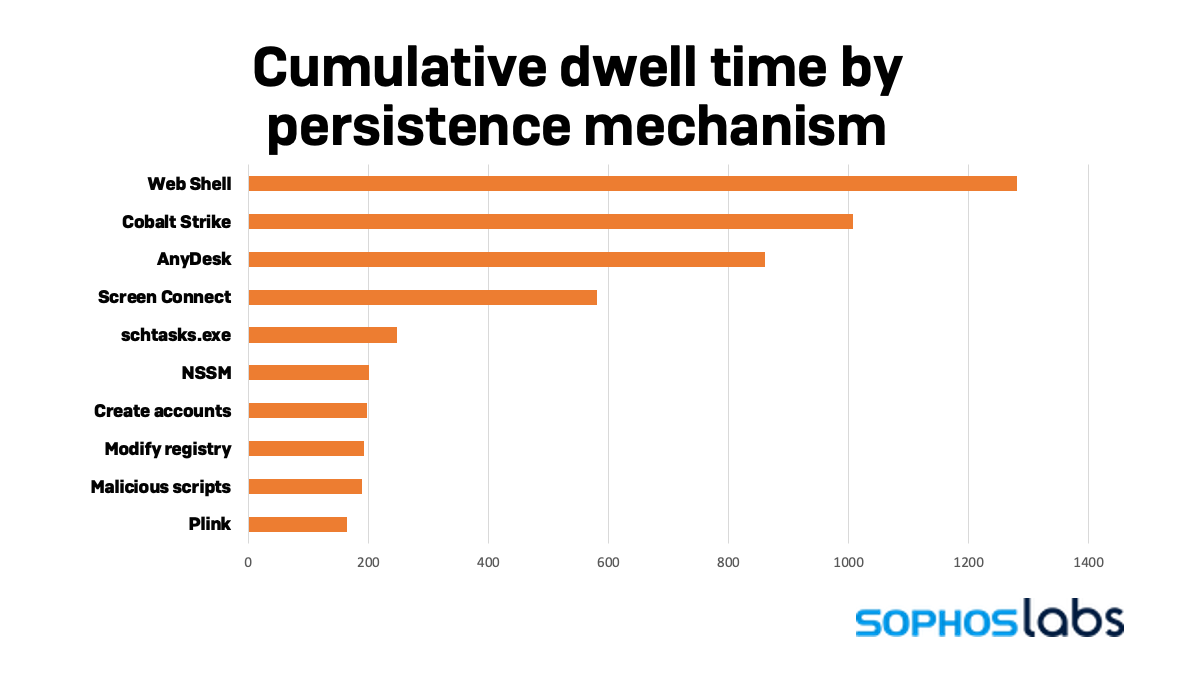
When looked at from a different angle, we see comparable results. The cumulative dwell time for victims, where the persistence mechanism was a web shell, showed a significantly higher total.
Of the 55 attacks which were observed using a web shell for persistence, 60% resulted in a ransomware attack, 38% in an intrusion with no clear motive, and 2% were cryptominers. The ransomware groups using web shells were once again dominated by Conti, which accounted for nearly half (48%) of web shells used in attacks. Other ransomware groups seen using web shells include AvosLocker, Black KingDom, BlackByte, Cuba, DarkSide, DoppelPaymer, Entropy, GlobeImposter, Karma, LockBit, Quantum, Ragnar Locker, and Ranzy.
Looked at another way, 78% of all network intrusions relied on web shells for persistence compared to 37% of all ransomware attacks. This signals that while ransomware groups don’t have to rely on web shells for persistence, they are quick to use them when presented with a widespread and easy to exploit vulnerability. For example, Conti affiliates were seen abusing the ProxyShell vulnerability within a few days after its publication to implant web shells on their victims.
In contrast, for run-of-the-mill compromises, web shells supplied reliable and continuous access to victims for a prolonged period. These attacks were likely performed by Initial Access Brokers (IAB) gathering inventory for resale to other criminals. Their aim is to secure a foothold in a victim before selling access to other adversaries, such as ransomware operators, to use in attacks, sometimes months after the initial intrusion. Widespread and easily exploited vulnerabilities like ProxyLogon and ProxyShell are a boon to IABs. What is unclear in the data is how much of the access was bespoke to the attack, versus bought from IABs, or the number of victims who would have succumbed to a ransomware attack, had they not discovered the initial compromise.
When controlling for web shells with respect to dwell time, there is a distinct drop in both the average (-20%) and median (-33%) values. Overall average dwell time for 2021 was 42 days, while the median was 15 days. If we remove web shells from the attack types, the average dwell time drops to 34 days, and the median drops to 10 days. It’s not surprising since web shells are meant to be stealthy and contribute to persistence.
Conclusions
As noted by CISA and other government security agencies, the ProxyLogon and ProxyShell vulnerabilities have been extensively exploited by adversaries in 2021. It’s therefore no surprise to see these vulnerabilities feature prominently in the data.
There are likely many latent ProxyLogon and/or ProxyShell breaches that are currently unknown. The fact is that for both vulnerabilities, patching does not remove existing web shells, it only removes the vulnerability. Where web shells have been implanted in victim networks, they might still be waiting until that access is used or sold.
Widespread, easy to exploit vulnerabilities like ProxyLogon and ProxyShell are two prime examples of why organizations need to prioritize patching of exposed services or move to cloud services (where patching is done automatically). Cybercriminals are quick to leverage these types of vulnerabilities, they persist for a long time, and the damage that results from a successful exploitation might not be apparent for months or years.