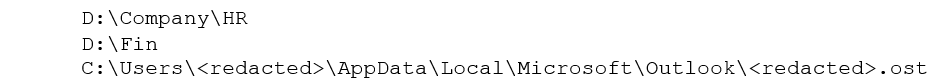Clop At The Top – But For How Long?
Credit to Author: Angela Gunn| Date: Mon, 10 Jul 2023 17:06:58 +0000
The Clop (or Cl0p) threat-actor group is a financially motivated organization believed to currently operate from Russian-speaking countries, though it was known to operate in both Russia and Ukraine prior to 2022. The Clop threat-actor group is linked to the groups identified as TA505 and FIN11. Its most characteristic ransomware, also called Clop or Cl0p, is a variant of the CryptoMix family, also thought to have been developed in the Russian Federation. MITRE identifies this ransomware as S0611. The group is currently in the news as the force behind the recent rash of attacks leveraging Progress Software’s MOVEit file-transfer system. The self-assigned “Clop” (Клоп) name, meanwhile, translates to “bedbug” – an adaptable, persistent pest.
Its involvement in the MOVEit exploitation is the third such effort ascribed to Clop during the first half of 2023, after the GoAnywhere incident in February and the PaperCut incident in April. Some of those efforts appear opportunistic, either resulting from a sale of the group’s own ransomware tooling or from collaboration with other groups. Others, such as MOVEit itself, appear to be the culmination of a long-term tech effort and refinement process by the group. We’ll look at the differences in approaches among the three later in this piece, but for now, the MOVEit thefts continue to unfold. Though it’s still not clear if even this campaign is truly successful: The group hasn’t provided many details about the current operation’s scale, but as recently as July 3, Sophos is not aware of any victims actually paying the ransom.
What is Clop?
Clop campaigns have historically targeted organizations in the United States, Canada, Latin America, Asia Pacific, and Europe for the most part. The group is known for its innovative techniques – it was, for instance, among the first to use the tactic of emailing customers and partners of a compromised site to demand that they, too, pressure the compromised target to pay – and aggressive, preferential targeting of large organizations. It’s part of infosec history as the source of the first known ransomware demand over $20 million USD, against Software AG in October 2020.
The group was first observed in 2019, relying then on phishing attempts, brute forcing, and the exploitation of known vulnerabilities. The group leverages a “double extortion” strategy, in which attackers steal users’ data and encrypt it; if the target of Clop’s attack refuses to pay the ransom, the attackers will not only refuse to restore access, but may also publish their personal data on the ‘CL0P^_- LEAKS’ site, which is accessible via Tor hidden service.
Clop’s preference for targeting larger companies (>$5 million/year revenue) and capitalizing on newer-but-disclosed vulnerabilities has been the primary driver of its success in the first half of 2023. The list of its current or recent victims is a who’s who of big names in industries including banking and financial services (BFSI), education, and (in an especially grotesque example of social engineering) healthcare. Clop is regularly connected to high-profile attacks such as the 2021 Accellion FTA (File Transfer Appliance) as well as GoAnywhere and the multi-vulnerability MOVEit. Of note is the group’s consistent and aggressive recent targeting of file-transfer services, which tend to handle data from a variety of systems and thus could be considered a vulnerable point in many supply chains.
How Do You Do, That Thing You Do? Let’s Talk Tactics
The Clop ransomware gang employs several tactics during an attack to maximize impact and increase the likelihood of victims paying the ransom. (The tactics and even the target’s experience may change from case to case, but money is almost always the goal. We’ll touch on certain exceptions below.) To understand how Clop typically executes its mission, we’ll step through highlights of a typical attack flow.
Initial Access
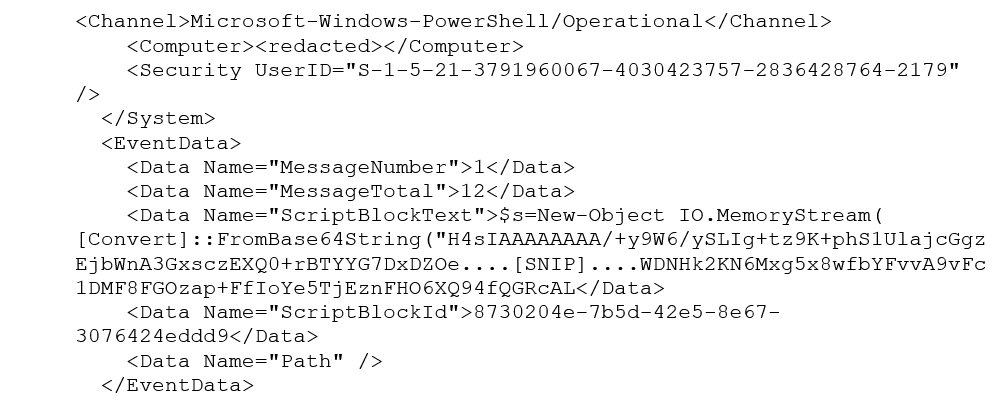
The Clop gang usually gains initial access to a victim’s network through phishing emails, exploit kits, or exploitation of vulnerabilities in software and systems. It often uses social engineering techniques such as spam, malicious links, and other lures in an effort to gain a foothold for its ransomware. And it can be persistent; one Sophos MDR client’s logs recorded 3,689 Clop-driven attempts against their Ubiquity UniFi server to gain initial access, as shown in the log snippet below.
In that case, the attacker was aiming at the Log4J vulnerability (CVE-2021-44228) and was willing to throw the kitchen sink at it; we observed payloads ranging from PoCs to Metasploit modules to exploits designed specifically for Linux hosts. The attacker was anything but stealthy in this spray-and-pray targeting.
Persistence
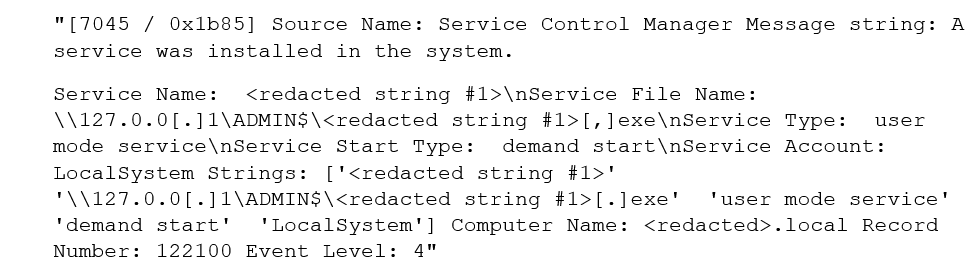
Clop maintains access to compromised systems in multiple ways. In a case recently handled by the Sophos X-Ops Incident Response team, the threat actor chose to leverage Cobalt Strike Beacon to establish their persistence on the first compromised machine, as seen in the log snippet below.
This activity was achieved by the creation of a new service, shown in the log snippet below executing the Cobalt Strike installer.
Lateral Movement
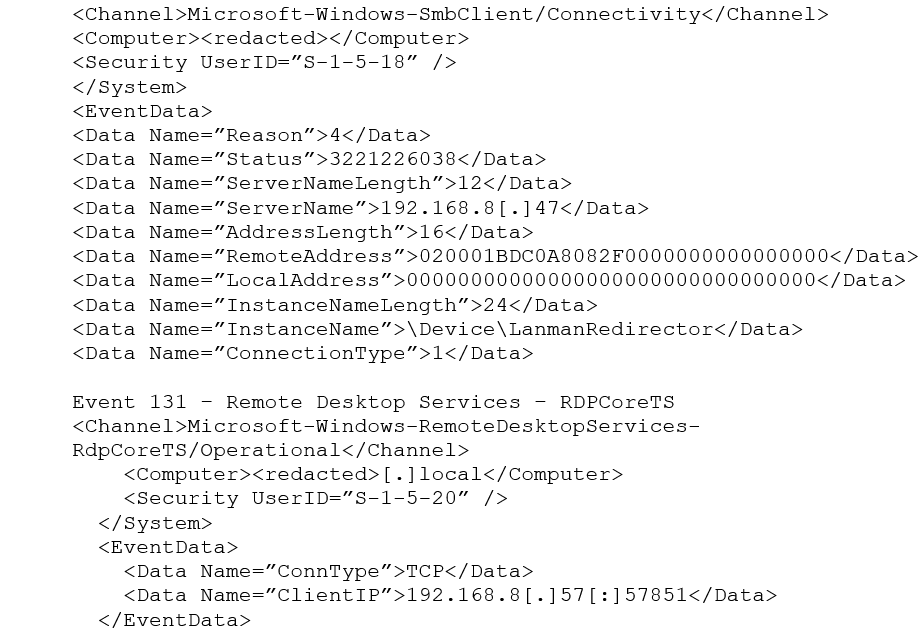
Once access to the network has been achieved, Clop pivots laterally, searching for and infecting connected systems. This lateral movement allows the ransomware to deploy quickly throughout the network: infecting the infrastructure, encrypting many files, and maximizing the impact of the operation. In incidents Sophos observed, the threat actor initially leveraged SMB connections before transitioning to interactive RDP sessions, as shown below.
Exfiltration
The Clop gang often exfiltrates data that it considers valuable from compromised networks before deploying the ransomware – including employee HR data, intellectual property, financial data, and customer information. This gives the group the leverage it needs to strengthen the extortion portion of the plot, relying on the threat of leaks to pressure victims into paying hefty ransoms. One of the tactics Clop and similar groups rely on most frequently for exfiltration is classified by MITRE as Exfiltration Over Web Service [T1567], which covers use of a variety of third-party tools such as megasync, rclone, Filezilla, or Windows Secure Copy. They also look at C2-based avenues of approach such as Remote Access Software [T1219] and Ingress Tool Transfer [T1105]. The example shown below provides insight into what types of information they [Clop] typically seek.
Data Encrypted for Impact
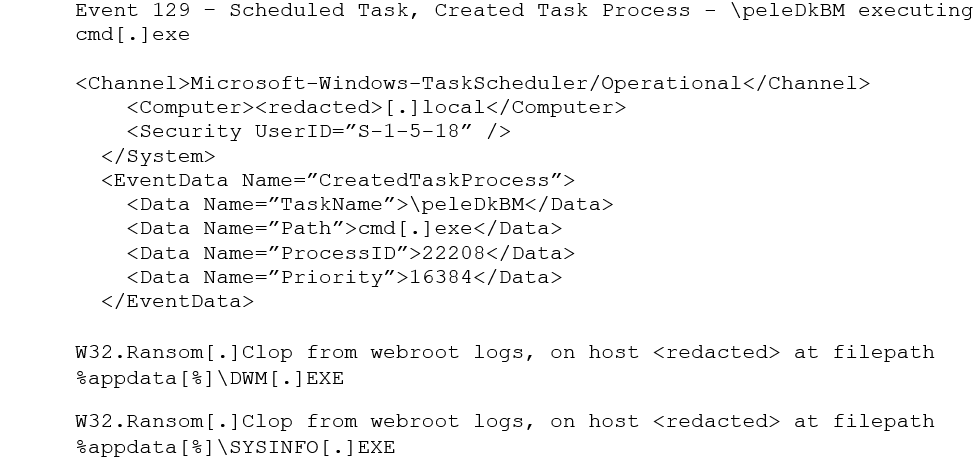
The primary focus of Clop ransomware is to encrypt files on the compromised systems, whatever the eventual outcome or demand on the attack target. It targets as many file types as possible, casting a large net. As we see below, a scheduled task is a convenient way for the threat actor to quickly deploy ransomware, in this case both dwm.exe and sysinfo.exe, across victim machines.
Victim Notification
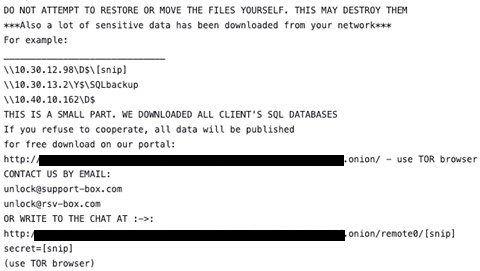
As is typical with ransomware operators, after encrypting (and possibly exfiltrating) the files, Clop leaves a README.TXT ransom note on the compromised systems. This is (usually) where the price to decrypt the files is made known to the target – a distinctive choice, since ransomware gangs often prefer to disclose the price to victims once a private chat is established — as well as the instructions for how to provide the payment demanded. Meanwhile, the attackers leave their mark all across the network, changing the extensions of the encrypted files to .Clop (or .CIIp or .C_L_O_P or similar). The image below shows a typical Clop ransomware note.
Figure 1: A message nobody wants to see on their network. (Image credit: https://github.com/threatlabz/ransomware_notes/blob/main/clop/clop2.txt)
Interestingly, there is variety in Clop’s ransom-note style. An example from January 2023, sourced by PCRisk and replicated in an HHS analysis of the attacks, differs greatly from the Github sample above – no mention of publication, a time limit of two weeks for the target to contact Clop via email, and pressure to respond quickly – “the final price depends on how fast you write to us.” This final aspect – a deadline for initial contact – has been used in the MOVEit attacks.
Network Denial of Service
There have been some instances, generally in hacktivism-related cases, where the Clop gang will also look to overwhelm the target’s network by DDoS, further impairing the targeted organization while they await payment. These hacktivism campaigns are not generally in line with Clop’s usual targeting and goals, and appear to be mainly undertaken against nation-state entities in tandem with affiliates. The benefit to Clop of participating in such campaigns (money, loyalty, or something else) is unknown, as is the actual impetus for the attack – hacktivism or merely ransomware with extra pressure points. (That said, nation-state activity is apparently not always appealing to the group. In the MOVEit attack, the group issued a statement in mid-June telling entities affected by the attack that “If you are a government, city or police service do not worry, we erased all your data. You do not need to contact us. We have no interest to expose such information.”)
Though these tactics make up the current Clop playbook, the group continues to evolve. This is what makes Clop so successful: The group has set methods of operation, but remains flexible in its ability to leverage additional techniques in order to demand more ransoms from a potentially vast list of targets.
Known Affiliations
The Clop ransomware gang is no stranger to collaboration during operations, including sharing resources and techniques. It has worked with a variety of allied groups in the cybercrime ecosystem including TA505 and FIN11 (to which, as mentioned above, Clop is “related”; a recent FBI / CISA alert states that Clop and TA505 are identical, though others suggest the three simply overlap or that FIN11 is a subset of TA505), as well as DarkSide and more recently FIN7. Some instances of collaboration have included point-of-sale attacks or plain old-fashioned exploitation. Clop’s brand of cybercrime fits in well with that of other bad actors. As such, its ransomware is often utilized by other high-profile groups, and is occasionally offered for sale on RaaS (ransomware-as-a-service) sites. In some situations, there is no prior known affiliation, but an observable overlap in techniques. overlap in techniques.
But What Have You Done for Me Lately?
In April 2023 we observed Clop exploiting vulnerable PaperCut servers, installing the same Truebot malware it used in the GoAnywhere attacks; Truebot is generally linked to the Silence Group. (PaperCut, from the company of the same name, is print-management software; GoAnywhere, from Fortra, does managed file transfer – as noted above, a noteworthy focus by the group.) This fits another pattern Sophos has seen with Clop over the past three years — leaning into known exploitation opportunities and seizing the initiative. The group relies on these opportunities for initial access and then pivots towards the next phase to retrieve the data it will eventually hold for ransom.
On the other hand, it’s possible that Clop’s hand in MOVEit stretches back – way back – and involves sustained tech effort and refinement. Following this exact approach to emerging vulnerabilities, the Clop ransomware gang claimed that it was behind the MOVEit Transfer data theft attacks and that it had been exploiting the vulnerability since May 27, 2023 – the day that CVE-2023-34362 exploitation activity first turned up in Sophos data, and four days before Progress disclosed the situation. But intriguingly, some reports hint that the group has been test-driving CVE-2023-34362 literally for years, perhaps as early as July 2021. The group hasn’t provided many details about the current operation’s scale, but as recently as July 3, Sophos is not aware of any victims paying the ransom.
So how does this end?
With their current momentum and based on what we’ve seen, Clop has a chance to continue to push the envelope in terms of scale and tactics employed, as long as its ransoms are being paid.
Law enforcement agencies and cybersecurity organizations have actively pursued legal action against the Clop gang. Over the last few years, several members of the group have been arrested or indicted, leading to temporary disruptions in its operations. However, this appears to have done little to slow the group’s momentum. Based on its history, it appears that Clop will likely continue to leverage vulnerabilities (patched and unpatched) and joint operations to expand its footprint. The group’s output indicates no current diminution in its staffing, skills, or ambition.
Mitigation Recommendations
Organizations are advised to take the following actions when looking to prevent Clop ransomware and similar attacks:
- Regularly patch and update software and applications to their latest versions, and perform vulnerability assessments periodically.
- Be mindful that pirated software can also lead to an increased probability of infection of your devices, since these are frequently used to spread malware.
- Conduct an inventory of assets and data.
- Focus on identifying authorized and unauthorized devices and software.
- Stay aware of lateral movements.
- Once attackers are inside your organization, they will try to move through the network infecting as many endpoints as they can. You can stop them more effectively by having visibility to spot this anomalous behavior. Analyzing netflows is usually the easiest way.
- Provide admin privileges and access only when necessary, establishing a software allow list that only executes legitimate applications.
Sophos’ Intercept X provides multiple layers of detection against the components and techniques used by Clop, including understanding of the relevant C2 frameworks and of the lateral movement seen with Clop-related attack attempts.
These recommendations should serve as a sounding board for actions that need to take place, in an effort to protect against Clop as well as other ransomware types. They will help to decrease the likelihood of exposure to malware and intrusion, and can help to protect your assets. By developing a consistent approach to security and awareness, while encouraging those within your organization to do the same, you are building an effective culture of operational security.
Acknowledgements
Sophos’ Mark Parsons, Colin Cowie, Benjamin Sollman, Morgan Demboski, and Paul Jaramillo contributed to this post.