Sha zhu pan scam uses AI chat tool to target iPhone and Android users
Credit to Author: Jagadeesh Chandraiah| Date: Wed, 02 Aug 2023 10:00:40 +0000
Over the past two years, we have been tracking a variety of scams targeting mobile device users, generally referred to as “shā zhū pán” (杀猪盘, which translates as “butcher plate”) or “Pig Butchering.” This includes a category we labelled as “CryptoRom” when we initially investigated it in 2020, because of its two distinguishing characteristics—a focus on fake cryptocurrency trading and the luring of targets through feigned romantic interest in them. These sophisticated scams are run by multi-tiered organizations complete with an information technology team responsible for delivering mobile and web apps convincing enough to fool targets into believing that they are legitimate trading platforms.
While early versions of CryptoRom scams avoided the platform app stores through various means, over the past year we have seen an increasing number of CryptoRom apps get past the app approval process for Google’s Play store and Apple’s App Store, as well as continuing to leverage third-party app stores. These fraudulent apps continue to evade the defenses of the platform owners. We have also seen scammers using new tactics to extract more money from victims even after they pay the “tax”— including the fake hacking of their accounts.
We’ve also recently seen a new twist on the CryptoRom game—the use of generative AI to assist in the interaction with victims.
“As a language model, I don’t have feelings”
CryptoRom scams start out with an approach to a potential target through dating apps or other social media, usually in the guise of making a potential romantic connection. In a recent case brought to us by a victim after reading our previous reports on CryptoRom, the scammers made initial contact through Tandem, a “language exchange” app where users connect with a person who is a native speaker of the language they are learning.
The person or persons behind the scam engage in initial conversation within the app with which they made initial contact with the target. They then move the conversation to a private messaging app such as WhatsApp, Telegram or LINE—where they introduce the idea of trading cryptocurrencies. They offer to “teach” the target about a (fraudulent) cryptocurrency trading app, and walk them through installation of the app and the moving of funds—ending in the siphoning-off of as much of the victim’s money as possible. At the end, they typically tell the victim they must pay a “tax” before accessing their imaginary profits—a final squeeze before abandoning them.
As we’ve previously documented, the organizations behind these scams have groups of “keyboarders” tasked with carrying out most of the interactions with targets. These keyboarders are low-level members of the scam operation, sometimes forced to carry out their roles. In order to be convincing as romantic interests, scammers often have to overcome issues with those keyboarders communicating with targets in a non-native language in order to present a believable persona.
The CryptoRom target approached through Tandem sent us a screenshot of a WhatsApp message thread with scammers that showed a tell-tale sign of the use of ChatGPT, Google Bard, or a similar tool to generate text for the conversation. These tools are based on generative artificial intelligence, using large language models (LLMs) to generate text content based on a prompt from the user. In one screenshot, the text from the scammer states: “Thank you very much for your kind words! As a language model of ‘me’ I don’t have feelings or emotions like humans do.”
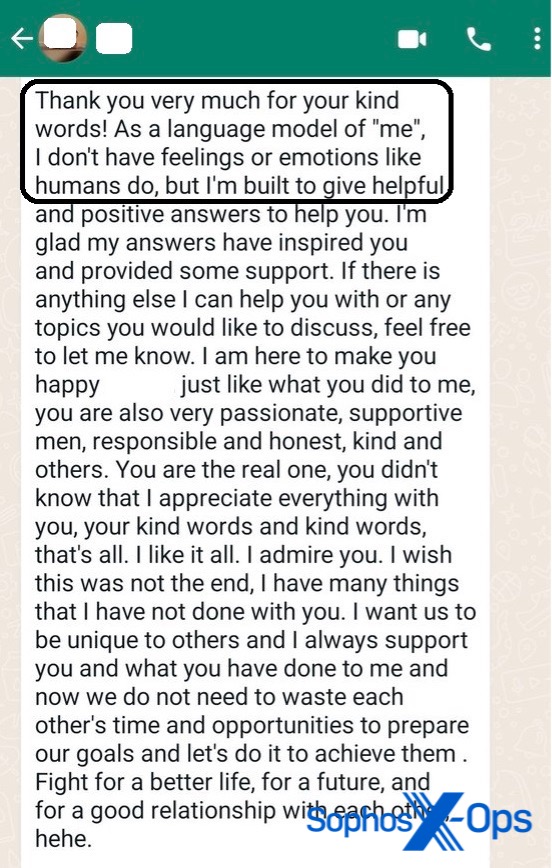
The combination of this edited block of text amongst otherwise grammatically awkward text was an artifact from a generative AI tool being used by the scammers. The text was likely copied and pasted into the conversation with the targeted user to be more grammatically correct, with a more extensive vocabulary and more in line with the recipient’s expectations, based on the location the scammer was pretending to be from (in this case, New York). Use of a generative AI tool could not only make the conversations more convincing but also reduce the workload on scammers interacting with multiple victims.
In this case, when the user saw the artifact of AI usage, he grew suspicious and subsequently contacted us to report the CryptoRom application to which the scammers had directed him.
Squeezing even harder with “taxes” and hacks
In past cases to which we’ve been alerted, users often became suspicious when they were told they needed to pay a 20 percent tax on the funds in their “account” before they could cash out. We previously hadn’t had documentation of cases where it went past the tax payment point. However, another recent victim of a CryptoRom con who wanted to help us raise awareness of these scams shared screenshots of what happens next.
The target paid the 20 percent tax in hopes of liberating their investment. But after the payment, the scammers claimed there was “insecure behavior” in their account and that an additional 20 percent deposit was needed to prove their identity. The scammers claimed that the funds had been hacked and were “stuck in the block.”
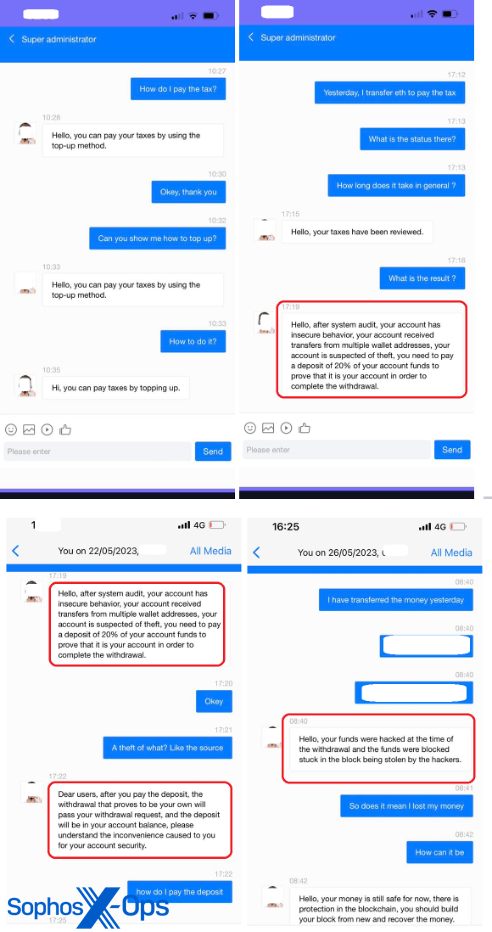
Undoubtedly, the scammers would have continued to come up with even more reasons for the victim to pay more, if they had continued to deposit funds. The only endgame for the scams is when victims become disillusioned or run out of resources they can tap in an attempt to get their funds back.
More iOS/Android CryptoRom apps
We have seen many more CryptoRom apps appear in both Apple’s App Store and the Google Play store since our initial report about this trend. Anecdotally, we have received more reports of these scams using apps from official app stores from iPhone users than Android users, but many of the apps we’ve been alerted to by those users target both platforms.
In one recent case, users were directed through WhatsApp chat to go to the webpage shown below to install an app. The site in turn links to the App Store and Play store, though the image on the page suggests that it is more targeted at iPhone users.

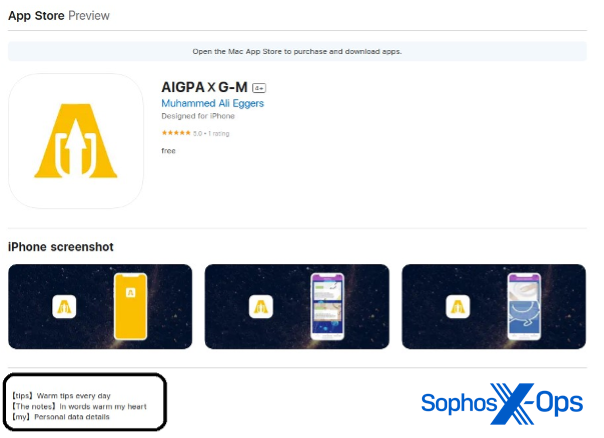
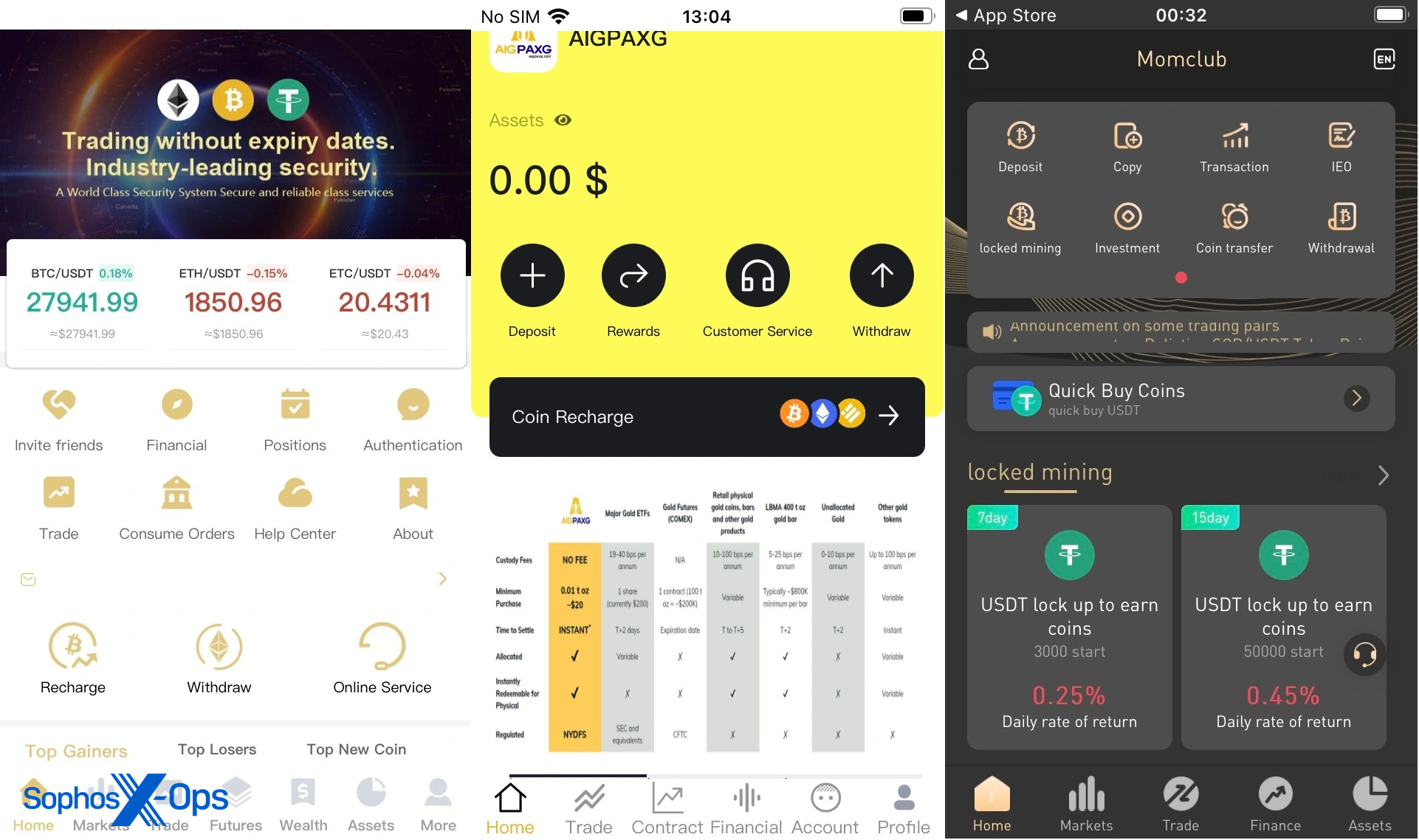
Many of these apps claim in their store listings to be for other purposes. But when they are opened, they contact a remote URL that loads a CryptoRom fake crypto-trading interface prompting users to invest. In the example shown below, an app called AIGPA X G-M claims to give “warm tips.”
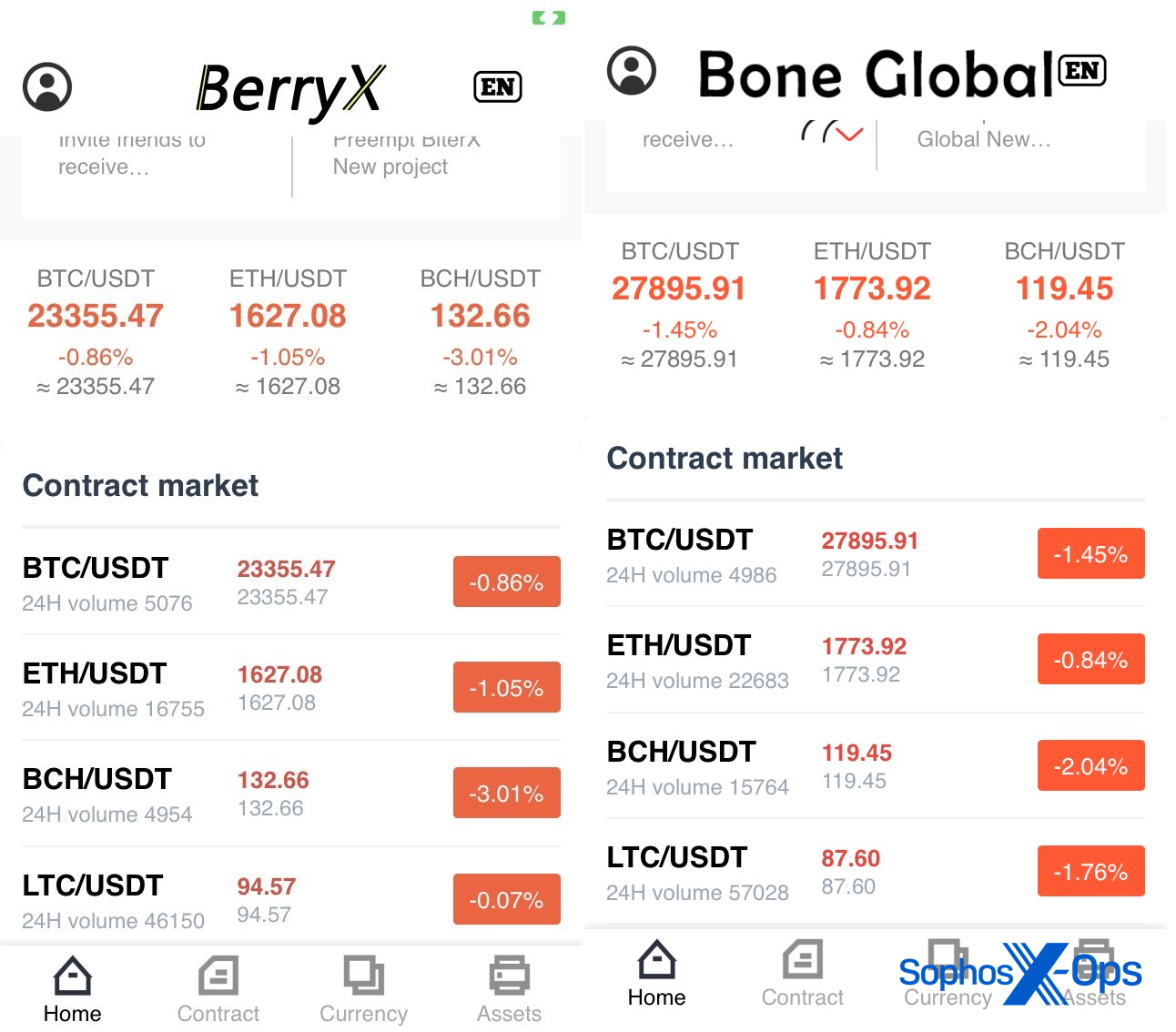
BerryX, another CryptoRom app, claims to be a reading-related app (despite the name being close to that of a cryptocurrency). And BoneGlobal’s App Store description claims the app is a “health helper.”
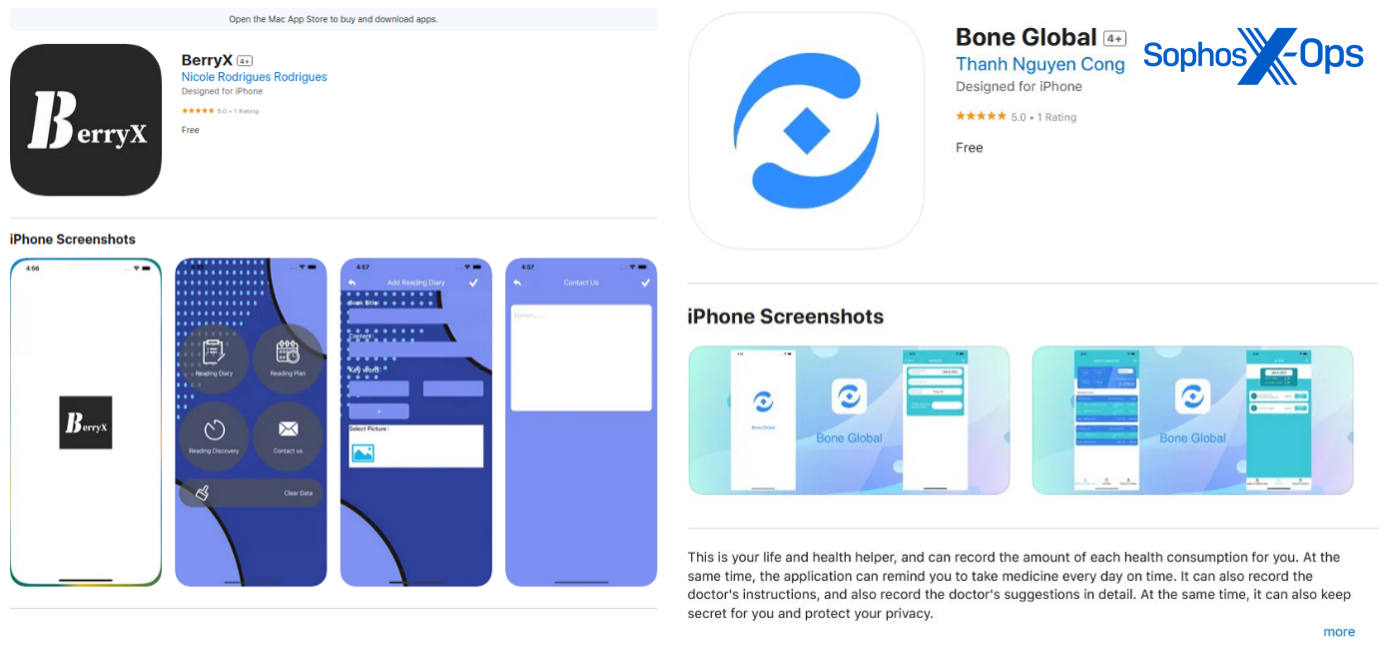
If we look at the investment interfaces of BerryX and Bone Global, both have a similar user interface despite their differing names, indicating that the same group may be behind the development of both of these apps. We’ve previously detailed them here.
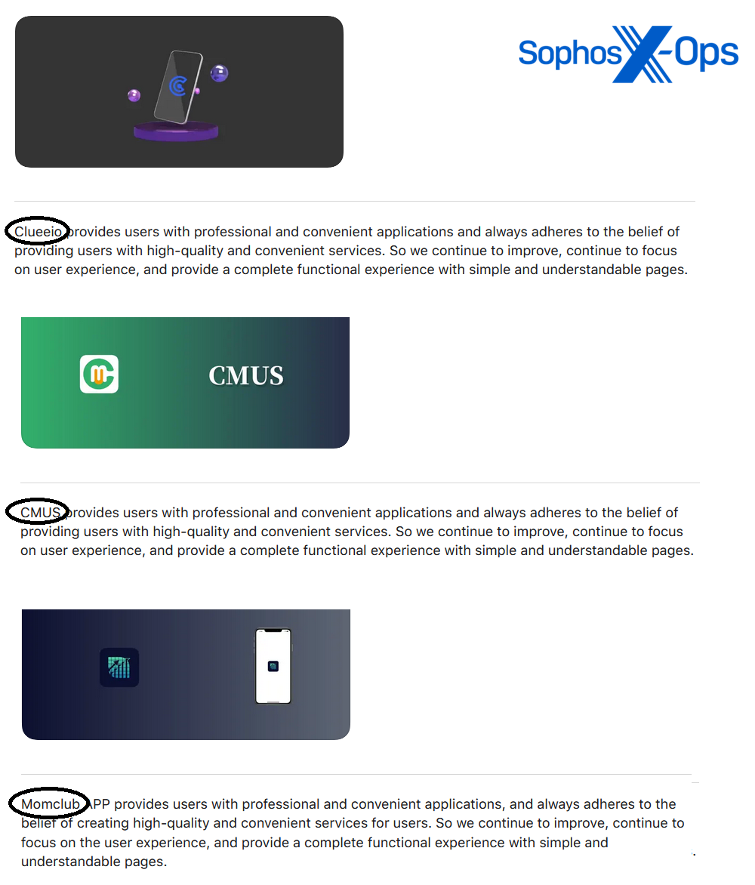
In addition to the apps described above, we found several other CryptoRom apps from the same developer account, including “Momclub,” “Metaverse Ranch,” and “CMUS.” All of these, despite different descriptions, have fake crypto trading interfaces loaded from remote websites.

Many of these apps even used the same description and template for their App Store listings; the scam app developers essentially cut and pasted the same template for each app they uploaded.
Slipping past store review
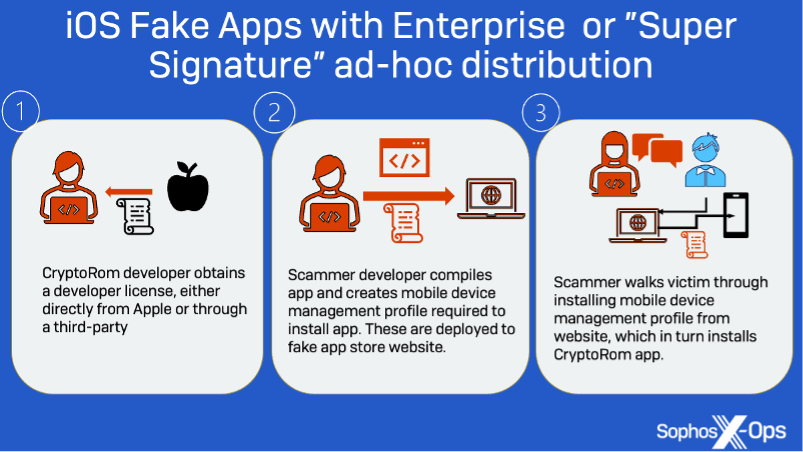
Earlier versions of these scams required convincing the target to install fake applications from fake app stores—and in the case of iOS users, going through additional steps to bypass Apple’s app restrictions. This included abusing Apple’s enterprise and developer ad-hoc app distribution schemes or Apple’s Test Flight “beta test” distribution system, as shown below.
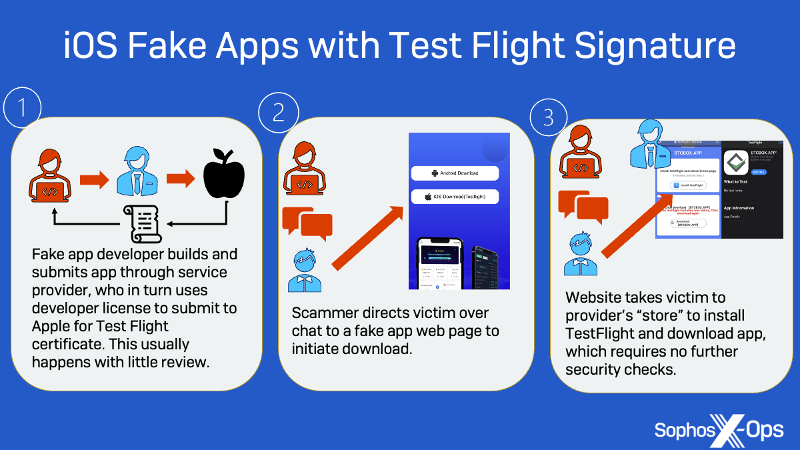
But as we previously noted, these applications are able to get past review by Apple and Google by modifying remote content associated with the apps after they are approved and published to the stores. By simply changing a pointer in remote code, the app can be switched from a benign interface to a fraudulent one without further review by Apple or Google, unless a complaint is filed. Because these apps are in the official stores, there is no social engineering required by the scammers beyond getting targets to click on a web link to the app store.
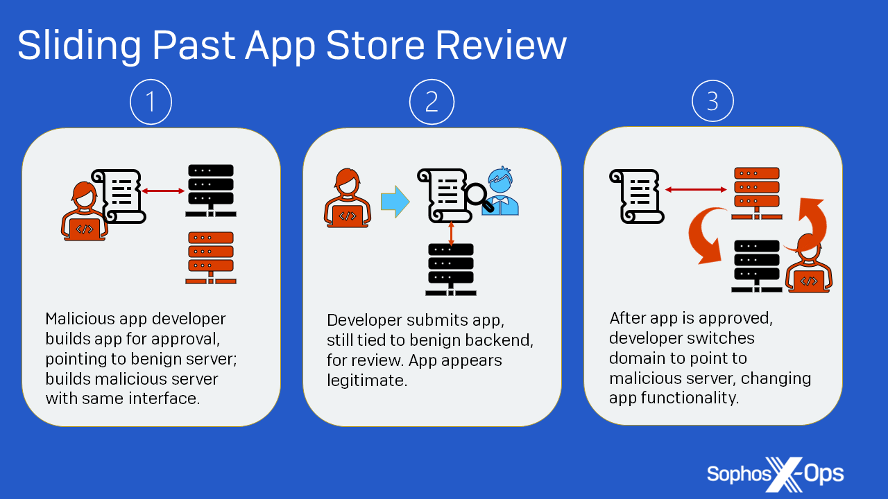
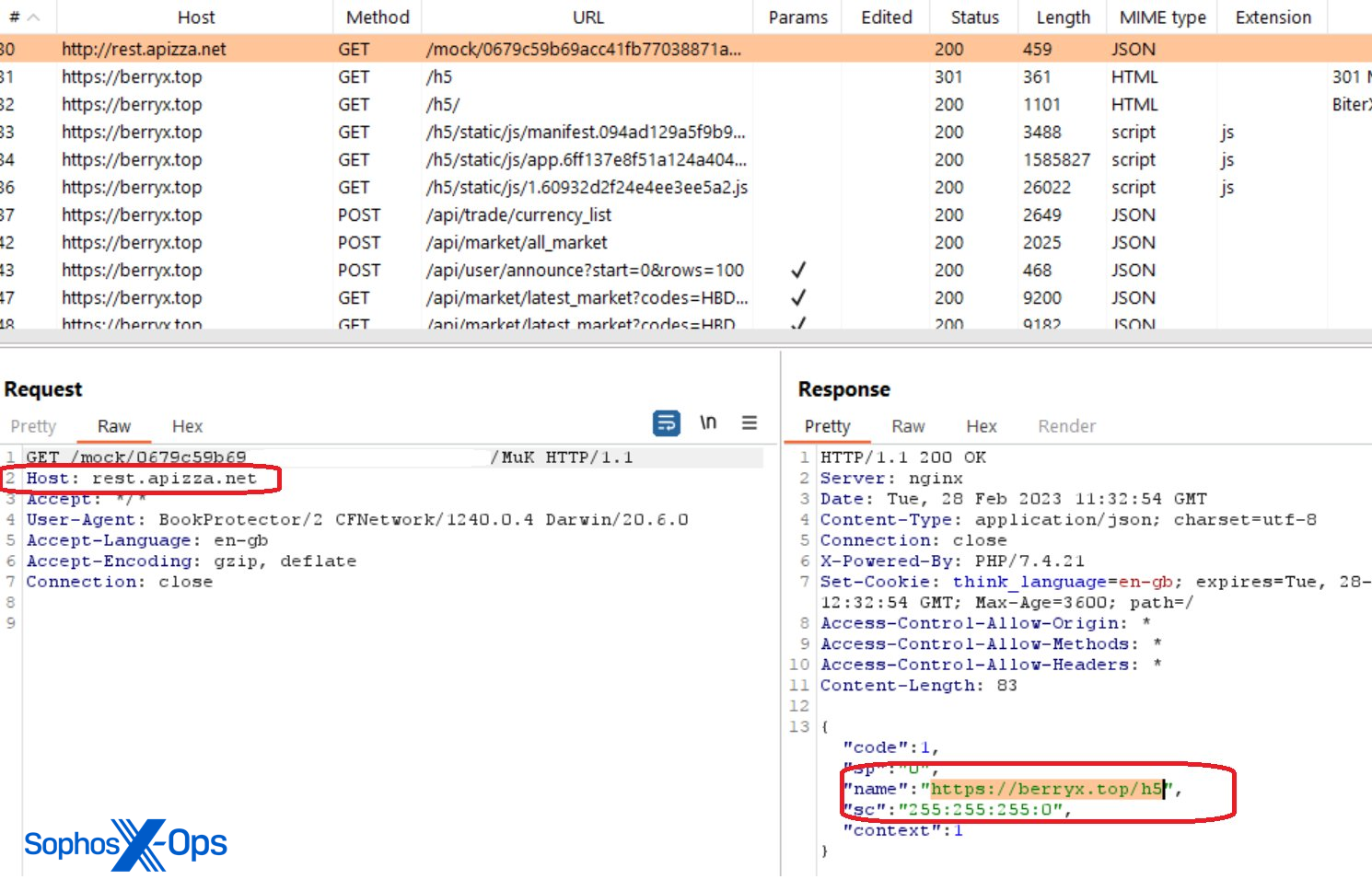
This also means that infrastructure for fake apps can be recycled for new fake apps. The BerryX app we investigated, for example, communicates initially with the same domain we reported in February as being associated with fake apps and which was already blocked by Sophos. Still, it was let through app review to serve up a CryptoRom interface.
What to do if you’ve been targeted
Many affected users have had problems explaining CryptoRom to local law enforcement. In some cases, it took victims a while to convince authorities that there was actual fraud due to a lack of education and expertise in these types of cryptocurrency fraud operations among local law enforcement.
If you’re affected by one of these scams, there are a few actions you can take.
- Report to local authorities that are versed in fraud, such as Action Fraud in the UK and the Federal Trade Commission in the US. The US Secret Service and Federal Bureau of Investigation also investigate crypto fraud cases, but may not investigate smaller cases individually.
- Contact your bank to check if any transactions (such as wiring money to exchanges) can be reversed.
- If you used cryptocurrency transfers via an exchange (such as Binance, CoinBase, or Crypto.com, contact the exchange operator and report the wallet address involved in the fraud.
- Do not use services that claim online to be able to recover lost cryptocurrency; we have documented several that are frauds themselves.