Step-by-step through the Money Message ransomware
Credit to Author: Angela Gunn| Date: Tue, 31 Oct 2023 19:56:34 +0000
In August 2023, the Sophos X-Ops Incident Response team was engaged to support an organization in Australia infected with Money Message ransomware. This attack vector, known for its stealth, does not append any file extensions to the encrypted data, making it harder for victims to identify the encrypted files simply by spotting such extensions.
In this post, we will look at the incident attack flow, illustrating how threat actors are deploying the Money Message ransomware and what measures can combat attacker efforts at various points along the MITRE ATT&CK chain.
Make a note of it
As part of its routine, the ransomware drops a ransom note named “money_message.log” directly into the root directory of the C: drive.
The ransom note on the target’s system read as follows:
Your files was encrypted by “Money message” profitable organization and can’t be accessed anymore.
If you pay ransom, you will get a decryptor to decrypt them. Don’t try to decrypt files yourself – in that case they will be damaged and unrecoverable.
For further negotiations open this <redacted>.onion/<redacted>
using tor browser https://www.torproject.org/download/
In case you refuse to pay, we will post the files we stole from your internal network, in our blog:
<redacted>.onion
Encrypted files can’t be decrypted without our decryption software.
<redacted>.onion/<redacted>
Attack Flow Details
Initial Access
Our investigation indicates that the attacker gained initial access via the target’s VPN, which was using single-factor authentication. This is an example of MITRE’s T1078 – Valid Accounts technique.
Guidance
Implementing multifactor authentication (MFA) for VPN connections is paramount to enhance security and thwart potential unauthorized access. Additionally, continuous monitoring of VPN logs and user activity should be in place to promptly detect any suspicious login attempts or anomalies. Upgrading to a more robust and layered authentication approach, such as MFA, is essential to bolster the first line of defense against potential threat actors seeking to exploit single-factor vulnerabilities and gain unauthorized VPN access.
Defense Evasion
The threat actor deployed GPO Policy to disable Windows Defender real-time protection. This is an example of MITRE’s T1562.001: Impair Defenses: Disable or Modify Tools sub-technique.
[HKEY_LOCAL_MACHINESoftwarePoliciesMicrosoftWindows Defender] DisableAntiSpyware: [REG_DWORD_LE] 1 [HKEY_LOCAL_MACHINESoftwarePoliciesMicrosoftWindows DefenderReal-time Protection] DisableRealtimeMonitoring: [REG_DWORD_LE] 1
Guidance
The first line of defense available to organizations is to use a security agent that has robust tamper protection. In terms of monitoring for this activity, these are detection-ready event sources. While it’s possible a system administrator would disable these protections (at least temporarily) during troubleshooting, given the risk of this activity, it’s something that should be investigated promptly if a corresponding support ticket isn’t found.
Lateral Movement
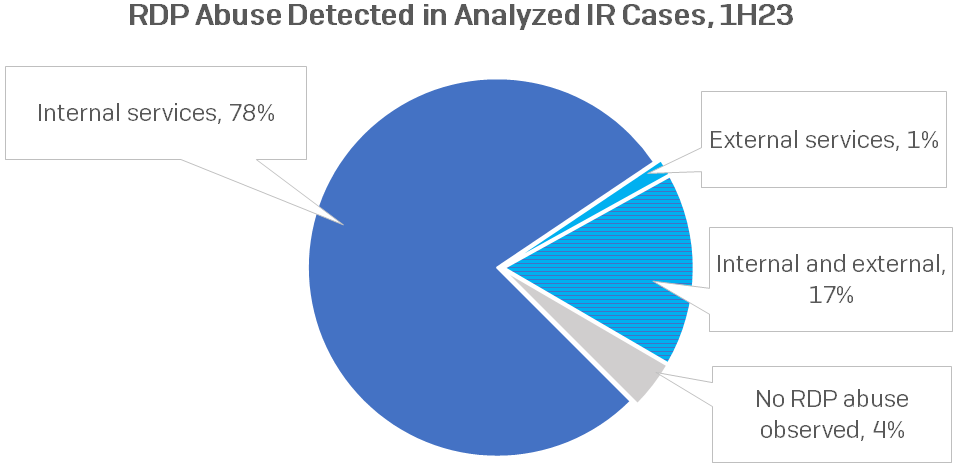
The threat actor leveraged psexec to run a batch script with the intention of enabling the RDP port, subsequently using Remote Desktop Protocol (RDP) to traverse the network. This is an example of MITRE’s T1021.001: Remote Services: Remote Desktop Protocol sub-technique. RDP is a common finding in cases handled by Incident Response, as shown by our findings from IR cases handled during the first half of 2023.
Figure 1: RDP abuse detections in IR cases for the first half of 2023
The batch script contents are as follows:
reg add "HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f Enable-NetFirewallRule -DisplayGroup 'Remote Desktop' netsh advfirewall firewall add rule name="Open Remote Desktop" protocol=TCP dir=in localport=3389 action=allow
Guidance
Securing RDP access can be difficult for many companies, but it is a project worthy of investment. The first item to check off the box is to restrict, by role, which accounts can access other systems using RDP. The overwhelming majority of users do not need this access. Secondly, adopting a centralized jump server, which only admins can access with MFA and blocking at the network level other system-to-system RDP is a strong preventative control. Lastly, a detection should be in place to promptly review anomalous RDP connections to deconflict them with approved system administration activity.
Credential Access
The threat actor, using Secretsdump.py (part of the Impacket toolkit), retrieved the SAM registry hive. This is an example of one way of executing MITRE’s T1003.002: OS Credential Dumping: Security Account Manager subtechnique.
C:WINDOWSsystem32svchost.exe -k localService -p -s RemoteRegistry
Guidance
It is crucial for organizations to prioritize the safeguarding of sensitive credentials. Implementing strong access controls, employing robust endpoint detection and response solutions, and monitoring for any suspicious activity related to SAM hive access are essential steps. Any unauthorized attempts to access or manipulate this critical system component should be promptly investigated, as they may indicate a breach or malicious activity that could compromise the security of sensitive credentials.
Collection
A confirmed compromised account was used to access sensitive folders like Finance, Payroll, SalesReport and HR in FileServer. MITRE lists 37 sub- and sub-sub-techniques under TA0009: Collection.
Guidance
Often by the time a threat actor is staging data, it’s too late to have a good security outcome. A good approach to prevent theft of data is to adopt least-privilege access, which means ensuring only the required people have access, followed by granular controls on exporting, sharing, or moving the files. DLP solutions, while having a history of being difficult to implement and maintain, are worth evaluating for high-risk data.
Exfiltration
The threat actor leveraged MEGAsync to exfiltrate the data. This is an example of MITRE’s T1567.002: Exfiltration Over Web Service: Exfiltration to Cloud Storage.
UserAssist entry: 87 Value name: C:Users<redacted>AppDataLocalTemp6MEGAsyncSetup32.exe Count: 1 User ”<redacted> registered Task Scheduler task “MEGAMEGAsync Update Task S-1-5-21-<redacted>"
Guidance
Organizations should focus on enhancing data loss prevention measures and network monitoring. Implementing robust outbound traffic analysis and content inspection can help identify and block suspicious data transfers. Furthermore, closely monitoring MEGAsync activities and detecting any unusual or unauthorized data transfers can be vital in mitigating data breaches. Rapidly investigate and respond to any signs of unauthorized exfiltration to prevent potential data compromise and minimize the impact on data confidentiality.
Impact
The threat actor leveraged two ransomware binaries, one for the Windows environment and one for the Linux environment. The Windows version is named windows.exe, and is detected as Troj/Ransom-GWD by Sophos. This is an example of MITRE’s T1486: Data Encrypted for Impact.
- The Money Message encryptor is written in C++ and includes an embedded JSON configuration file which contains some key details like what folders to block from encrypting, what extension to append, what services and processes to terminate, and domain login names and passwords likely used to encrypt other devices.
- The encryptor uses the ChaCha Quarter Round algorithm and ECDH encryption
- The ransomware creates the C:money_message.log ransom note when complete
- On endpoints protected with Sophos, the following detection is triggered:
Malware detected: ‘Troj/Ransom-GWD’ at ‘C:Users<redacted>AppDataLocalTemp6windows.exe’
The Linux variant is named ‘esxi’, Upon execution it will delete all the virtual hard disks. This is an example of MITRE’s T1561: Disk Wipe.
Commands executed on ESXi host:
cd /tmp/ chmod 777 esxi dir ls ./esxi
Guidance
As mentioned earlier, at this late stage in the attack, having full coverage on all systems with a properly configured XDR solution is vital to protect organizations from ransomware. In the case of Sophos, it’s critical for customers to have their CryptoGuard policy activated, which is something support can guide customers on.
Conclusion
The Money Message attackers’ path to exfiltration conforms to a fairly typical MITRE ATT&CK chain, as we have shown above. Though this particular attacker tries to muddy the waters for defenders, good defense – especially in the early stages – can provide an effective toolkit against bad outcomes.