2024’s first Patch Tuesday steps lightly
Credit to Author: Angela Gunn| Date: Tue, 09 Jan 2024 22:03:14 +0000
January isn’t traditionally the lightest month on patch managers’ calendars, so a second month of (relatively) few Microsoft releases is a bit of a treat. On Tuesday the company released 48 CVEs, including 38 for Windows. Eight other product groups or tools are also affected. Of the CVEs addressed, just two are considered Critical in severity by Microsoft; both affect Windows.
At patch time, none of the issues are known to be under exploit in the wild, and none have been publicly disclosed. However, nine of the addressed vulnerabilities in Windows and SharePoint (including one of the Critical-severity CVEs, affecting Kerberos) are by the company’s estimation more likely to be exploited in the next 30 days. Four of those are amenable to detection by Sophos protections, and we include information on those in a table below.
In addition to the 48 patches the release included information on four Chrome CVEs (released last week) that affect Edge, and one MITRE-issued CVE touching the open-source database engine SQLite. (There are no Adobe offerings this month.) We don’t include those issues in the CVE counts and graphics below, but we provide information on everything in an appendix at the end of the article. We are as usual including at the end of this post three other appendices listing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product family.
By the numbers
- Total Microsoft CVEs: 48
- Total Microsoft advisories shipping in update: 0
- Total Edge / Chrome issues covered in update: 4
- Publicly disclosed: 0
- Exploited: 0
- Severity
- Critical: 2
- Important: 46
- Impact
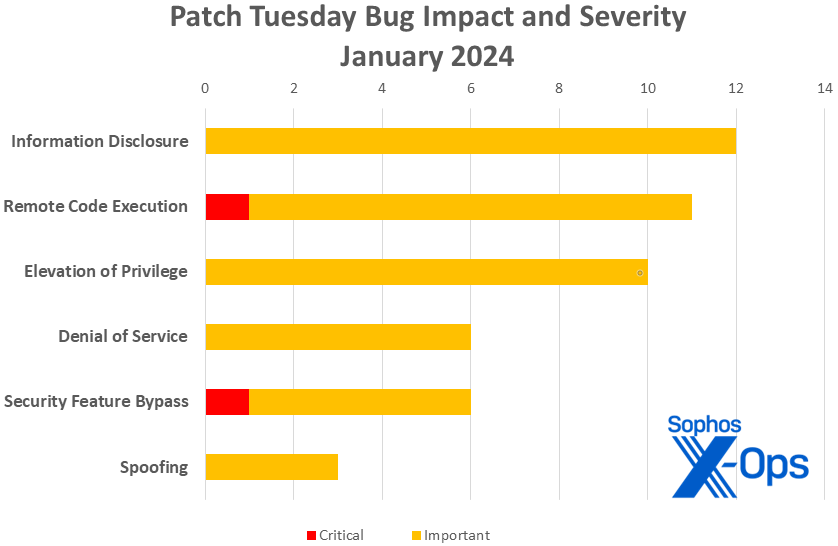
- Information Disclosure: 12
- Remote Code Execution: 11
- Elevation of Privilege: 10
- Denial of Service: 6
- Security Feature Bypass: 6
- Spoofing: 3
Figure 1: You’re reading the labels correctly: Information-disclosure issues outnumber both EoP and RCE bugs in January. Security feature bypass issues – one of them Critical-severity — also make a strong showing
Products
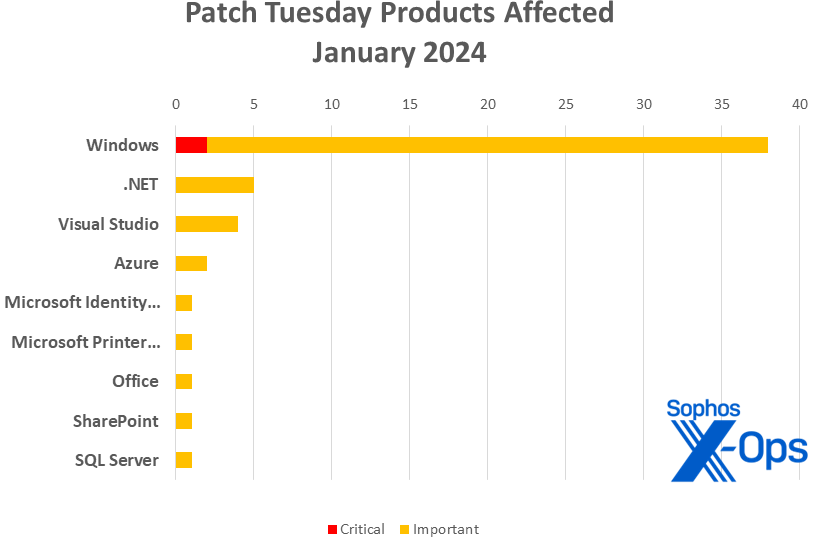
- Windows: 38
- .NET: 5 (including on shared with Visual Studio; one shared with Microsoft Identity Model / NuGet and Visual Studio; and one shared with Azure, SQL Server, and Visual Studio)
- Visual Studio: 4 (including one shared with .NET; one shared with .NET and Microsoft Identity Model / NuGet; and one shared with .NET, Azure, and SQL Server)
- Azure: 2 (including one shared with .NET, SQL Server, and Visual Studio)
- Microsoft Identity Model / NuGet: 1 (shared with .NET and Visual Studio)
- Microsoft Printer Metadata Troubleshooter Tool: 1
- Office: 1
- SharePoint: 1
- SQL Server: 1 (shared with .NET, Azure, and Visual Studio)
Figure 2: Windows is heavily represented in this month’s patches, but several less-familiar tools and applications are also in the mix (full names shown in tables below)
Notable January updates
In addition to the issues discussed above, a few specific items are worth noting.
CVE-2024-0057 — .NET, .NET Framework, and Visual Studio Framework Security Feature Bypass Vulnerability
CVE-2024-20674 — Windows Kerberos Security Feature Bypass VulnerabilityOf this pair of security feature bypass issues, Microsoft deems only the Kerberos issue to be Critical-class. The CVSS scoring system begs to differ, since the guide to that scoring system requires that scorers consider feasible worst-case scenarios when evaluating bugs in software libraries. Their CVSS base scores are thus 9.1 and 9.0 respectively. In any case, admins are encouraged to prioritize these two patches.
CVE-2024-20696 – Windows Libarchive Remote Code Execution Vulnerability
CVE-2024-20697 – Windows Libarchive Remote Code Execution VulnerabilityThe information available on these two identically named Important-class RCEs is scant, but there’s a big clue to their importance in the title: These two issues affect Libarchive, the engine for reading and writing in various compression and archive formats.
CVE-2024-20666 – BitLocker Security Feature Bypass Vulnerability
Another security feature bypass, this time in a security feature. This issue stands out for some fairly nuanced requirements around servicing the Safe OS; for most versions of Windows 11 this is now a fully automated process, and those relying on WSUS are automatically updated, but those working in more complex environments are strongly encouraged to check Microsoft’s published guidance for specific instructions. In any case, the attacker requires physical access to the targeted machine.
CVE-2024-21305 — Hypervisor-Protected Code Integrity (HVCI) Security Feature Bypass Vulnerability
The CVE with the lowest CVSS base score this month has something in common with the two highest-scoring CVEs: It’s yet another security feature bypass. This one, however, rates a mere 4.4 base score and requires the attacker to have physical access to the targeted machine and to have previously compromised admin credentials. It affects an assortment of Windows client and server versions and, for those still running that hardware, 15 versions of the Surface.
Sophos protections
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This is a list of January patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE.
Information Disclosure (12 CVEs)
Important severity CVE-2024-0056 Microsoft.Data.SqlClient and System.Data.SqlClient SQL Data Provider Information Disclosure Vulnerability CVE-2024-20660 Windows Message Queuing Client Information Disclosure Vulnerability CVE-2024-20662 Windows Online Certificate Status Protocol (OCSP) Information Disclosure Vulnerability CVE-2024-20663 Windows Message Queuing Client (MSMQC) Information Disclosure CVE-2024-20664 Microsoft Message Queuing Client Information Disclosure Vulnerability CVE-2024-20680 Windows Message Queuing Client (MSMQC) Information Disclosure CVE-2024-20691 Windows Themes Information Disclosure Vulnerability CVE-2024-20692 Microsoft Local Security Authority Subsystem Service Information Disclosure Vulnerability CVE-2024-20694 Windows CoreMessaging Information Disclosure Vulnerability CVE-2024-21311 Windows Cryptographic Services Information Disclosure Vulnerability CVE-2024-21313 Windows TCP/IP Information Disclosure Vulnerability CVE-2024-21314 Windows Message Queuing Client (MSMQC) Information Disclosure Remote Code Execution (11 CVEs)
Critical severity CVE-2024-20700 Windows Hyper-V Remote Code Execution Vulnerability Important severity CVE-2024-20654 Microsoft ODBC Driver Remote Code Execution Vulnerability CVE-2024-20655 Microsoft Online Certificate Status Protocol (OCSP) Remote Code Execution Vulnerability CVE-2024-20676 Azure Storage Mover Remote Code Execution Vulnerability CVE-2024-20677 Microsoft Office Remote Code Execution Vulnerability CVE-2024-20682 Windows Cryptographic Services Remote Code Execution Vulnerability CVE-2024-20696 Windows Libarchive Remote Code Execution Vulnerability CVE-2024-20697 Windows Libarchive Remote Code Execution Vulnerability CVE-2024-21307 Remote Desktop Client Remote Code Execution Vulnerability CVE-2024-21318 Microsoft SharePoint Server Remote Code Execution Vulnerability CVE-2024-21325 Microsoft Printer Metadata Troubleshooter Tool Remote Code Execution Vulnerability Elevation of Privilege (10 CVEs)
Important severity CVE-2024-20653 Microsoft Common Log File System Elevation of Privilege Vulnerability CVE-2024-20656 Visual Studio Elevation of Privilege Vulnerability CVE-2024-20657 Windows Group Policy Elevation of Privilege Vulnerability CVE-2024-20658 Microsoft Virtual Hard Disk Elevation of Privilege Vulnerability CVE-2024-20681 Windows Subsystem for Linux Elevation of Privilege Vulnerability CVE-2024-20683 Win32k Elevation of Privilege Vulnerability CVE-2024-20686 Win32k Elevation of Privilege Vulnerability CVE-2024-20698 Windows Kernel Elevation of Privilege Vulnerability CVE-2024-21309 Windows Kernel-Mode Driver Elevation of Privilege Vulnerability CVE-2024-21310 Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability Denial of Service (6 CVEs)
Important severity CVE-2024-20661 Microsoft Message Queuing Denial of Service Vulnerability CVE-2024-20672 .NET Core and Visual Studio Denial of Service Vulnerability CVE-2024-20687 Microsoft AllJoyn API Denial of Service Vulnerability CVE-2024-20699 Windows Hyper-V Denial of Service Vulnerability CVE-2024-21312 .NET Framework Denial of Service Vulnerability CVE-2024-21319 Microsoft Identity Denial of Service Vulnerability Security Feature Bypass (6 CVEs)
Critical severity CVE-2024-20674 Windows Kerberos Security Feature Bypass Vulnerability Important Severity CVE-2024-0057 .NET, .NET Framework, and Visual Studio Framework Security Feature Bypass Vulnerability CVE-2024-20652 Windows HTML Platforms Security Feature Bypass Vulnerability CVE-2024-20666 BitLocker Security Feature Bypass Vulnerability CVE-2024-21305 Hypervisor-Protected Code Integrity (HVCI) Security Feature Bypass Vulnerability CVE-2024-21316 Windows Server Key Distribution Service Security Feature Bypass Spoofing (3 CVEs)
Important severity CVE-2024-20690 Windows Nearby Sharing Spoofing Vulnerability CVE-2024-21306 Microsoft Bluetooth Driver Spoofing Vulnerability CVE-2024-21320 Windows Themes Spoofing Vulnerability Appendix B: Exploitability
This is a list of the January CVEs judged by Microsoft to be more likely to be exploited in the wild within the first 30 days post-release. Each list is further arranged by CVE. No CVEs addressed in the January patch collection are known to be under active exploit in the wild yet.
Exploitation more likely within 30 days CVE-2024-20652 Windows HTML Platforms Security Feature Bypass Vulnerability CVE-2024-20653 Microsoft Common Log File System Elevation of Privilege Vulnerability CVE-2024-20674 Windows Kerberos Security Feature Bypass Vulnerability CVE-2024-20683 Win32k Elevation of Privilege Vulnerability CVE-2024-20686 Win32k Elevation of Privilege Vulnerability CVE-2024-20698 Windows Kernel Elevation of Privilege Vulnerability CVE-2024-21307 Remote Desktop Client Remote Code Execution Vulnerability CVE-2024-21310 Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability CVE-2024-21318 Microsoft SharePoint Server Remote Code Execution Vulnerability Appendix C: Products Affected
This is a list of December’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE. Patches that are shared among multiple product families are listed multiple times, once for each product family.
Windows (38 CVEs)
Critical severity CVE-2024-20674 Windows Kerberos Security Feature Bypass Vulnerability CVE-2024-20700 Windows Hyper-V Remote Code Execution Vulnerability Important severity CVE-2024-20652 Windows HTML Platforms Security Feature Bypass Vulnerability CVE-2024-20653 Microsoft Common Log File System Elevation of Privilege Vulnerability CVE-2024-20654 Microsoft ODBC Driver Remote Code Execution Vulnerability CVE-2024-20655 Microsoft Online Certificate Status Protocol (OCSP) Remote Code Execution Vulnerability CVE-2024-20657 Windows Group Policy Elevation of Privilege Vulnerability CVE-2024-20658 Microsoft Virtual Hard Disk Elevation of Privilege Vulnerability CVE-2024-20660 Windows Message Queuing Client Information Disclosure Vulnerability CVE-2024-20661 Microsoft Message Queuing Denial of Service Vulnerability CVE-2024-20662 Windows Online Certificate Status Protocol (OCSP) Information Disclosure Vulnerability CVE-2024-20663 Windows Message Queuing Client (MSMQC) Information Disclosure CVE-2024-20664 Microsoft Message Queuing Client Information Disclosure Vulnerability CVE-2024-20666 BitLocker Security Feature Bypass Vulnerability CVE-2024-20680 Windows Message Queuing Client (MSMQC) Information Disclosure CVE-2024-20681 Windows Subsystem for Linux Elevation of Privilege Vulnerability CVE-2024-20682 Windows Cryptographic Services Remote Code Execution Vulnerability CVE-2024-20683 Win32k Elevation of Privilege Vulnerability CVE-2024-20686 Win32k Elevation of Privilege Vulnerability CVE-2024-20687 Microsoft AllJoyn API Denial of Service Vulnerability CVE-2024-20690 Windows Nearby Sharing Spoofing Vulnerability CVE-2024-20691 Windows Themes Information Disclosure Vulnerability CVE-2024-20692 Microsoft Local Security Authority Subsystem Service Information Disclosure Vulnerability CVE-2024-20694 Windows CoreMessaging Information Disclosure Vulnerability CVE-2024-20696 Windows Libarchive Remote Code Execution Vulnerability CVE-2024-20697 Windows Libarchive Remote Code Execution Vulnerability CVE-2024-20698 Windows Kernel Elevation of Privilege Vulnerability CVE-2024-20699 Windows Hyper-V Denial of Service Vulnerability CVE-2024-21305 Hypervisor-Protected Code Integrity (HVCI) Security Feature Bypass Vulnerability CVE-2024-21306 Microsoft Bluetooth Driver Spoofing Vulnerability CVE-2024-21307 Remote Desktop Client Remote Code Execution Vulnerability CVE-2024-21309 Windows Kernel-Mode Driver Elevation of Privilege Vulnerability CVE-2024-21310 Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability CVE-2024-21311 Windows Cryptographic Services Information Disclosure Vulnerability CVE-2024-21313 Windows TCP/IP Information Disclosure Vulnerability CVE-2024-21314 Windows Message Queuing Client (MSMQC) Information Disclosure CVE-2024-21316 Windows Server Key Distribution Service Security Feature Bypass CVE-2024-21320 Windows Themes Spoofing Vulnerability .NET (5 CVEs)
Important severity CVE-2024-0056 Microsoft.Data.SqlClient and System.Data.SqlClient SQL Data Provider Information Disclosure Vulnerability CVE-2024-0057 .NET, .NET Framework, and Visual Studio Framework Security Feature Bypass Vulnerability CVE-2024-20672 .NET Core and Visual Studio Denial of Service Vulnerability CVE-2024-21312 .NET Framework Denial of Service Vulnerability CVE-2024-21319 Microsoft Identity Denial of Service Vulnerability Visual Studio (4 CVEs)
Important severity CVE-2024-0056 Microsoft.Data.SqlClient and System.Data.SqlClient SQL Data Provider Information Disclosure Vulnerability CVE-2024-0057 .NET, .NET Framework, and Visual Studio Framework Security Feature Bypass Vulnerability CVE-2024-20656 Visual Studio Elevation of Privilege Vulnerability CVE-2024-21319 Microsoft Identity Denial of Service Vulnerability Azure (2 CVEs)
Important severity CVE-2024-0056 Microsoft.Data.SqlClient and System.Data.SqlClient SQL Data Provider Information Disclosure Vulnerability CVE-2024-20676 Azure Storage Mover Remote Code Execution Vulnerability Microsoft Identity Model (1 CVE)
Important severity CVE-2024-21319 Microsoft Identity Denial of Service Vulnerability Microsoft Printer Metadata Troubleshooter Tool (1 CVE)
Important severity CVE-2024-21325 Microsoft Printer Metadata Troubleshooter Tool Remote Code Execution Vulnerability Office (1 CVE)
Important severity CVE-2024-20677 Microsoft Office Remote Code Execution Vulnerability SharePoint (1 CVE)
Important severity CVE-2024-21318 Microsoft SharePoint Server Remote Code Execution Vulnerability SQL Server (1 CVE)
Important severity CVE-2024-0056 Microsoft.Data.SqlClient and System.Data.SqlClient SQL Data Provider Information Disclosure Vulnerability Appendix D: Advisories and Other Products
This is a list of advisories and information on other relevant CVEs in the December Microsoft release, sorted by product.
Relevant to Edge / Chromium (4 CVEs)
CVE-2024-0222 Chromium: CVE-2024-0222 Use after free in ANGLE CVE-2024-0223 Chromium: CVE-2024-0223 Heap buffer overflow in ANGLE CVE-2024-0224 Chromium: CVE-2024-0224 Use after free in WebAudio CVE-2024-0225 Chromium: CVE-2024-0225 Use after free in WebGPU Relevant to Windows (third-party product) (one CVE)
CVE-2022-35737 MITRE: CVE-2022-35737 SQLite allows an array-bounds overflow