Ten Years Later, New Clues in the Target Breach
Credit to Author: BrianKrebs| Date: Thu, 14 Dec 2023 17:51:39 +0000
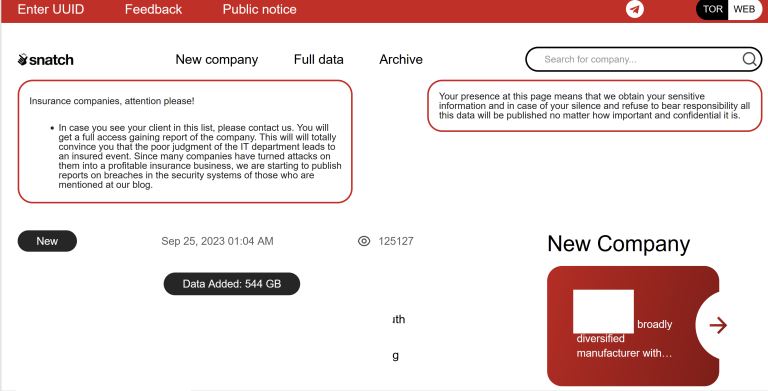
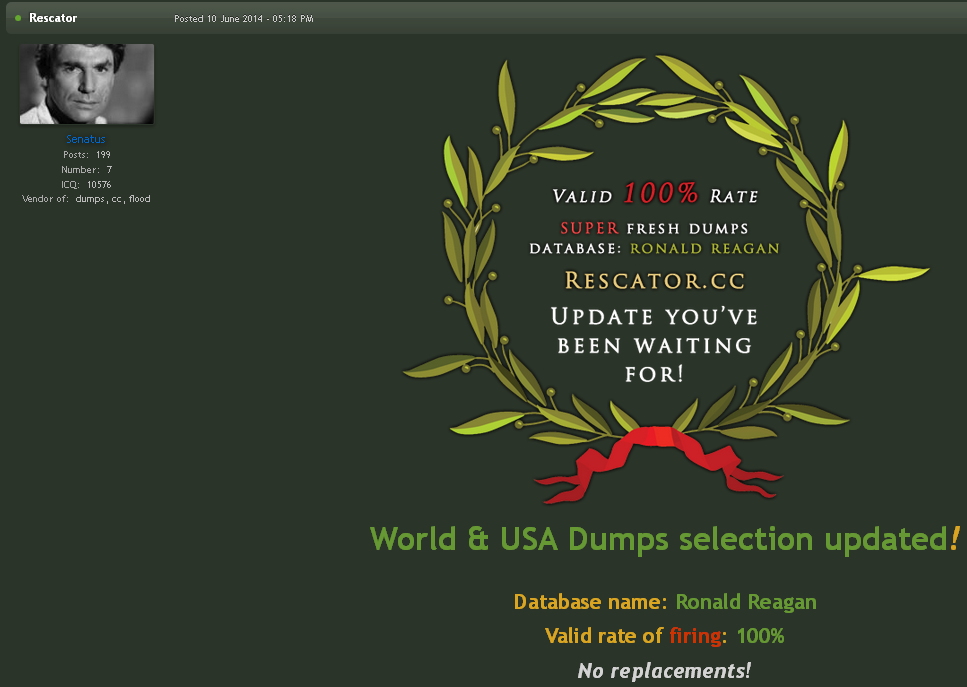
On Dec. 18, 2013, KrebsOnSecurity broke the news that U.S. retail giant Target was battling a wide-ranging computer intrusion that compromised more than 40 million customer payment cards over the previous month. The malware used in the Target breach included the text string “Rescator,” which also was the handle chosen by the cybercriminal who was selling all of the cards stolen from Target customers. Ten years later, KrebsOnSecurity has uncovered new clues about the real-life identity of Rescator.
Read more